Microsoft has recently acknowledged a critical security flaw in the Microsoft Support Diagnostic Tool, also known as MSDT, that comes pre-loaded with Windows.
Documented in CVE-2022-30190, the vulnerability allows an attacker to eventually be able to install apps or even create new accounts on the impacted devices.
While Microsoft doesn’t specifically name the Windows versions that are affected, the flaw exists in Microsoft Support Diagnostic Tool, so as long as the operating system comes with this application, it’s exposed as well.
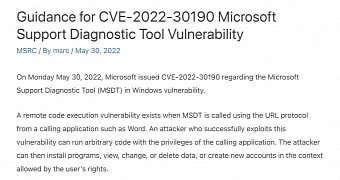
“A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights,” Microsoft says.
The workaround currently available
Microsoft says that users can just disable the MSDT URL protocol to block any exploit aimed at this vulnerability.
“Disabling MSDT URL protocol prevents troubleshooters being launched as links including links throughout the operating system. Troubleshooters can still be accessed using the Get Help application and in system settings as other or additional troubleshooters,” the company further notes.
In addition, the software giant says that Microsoft Defender, the antivirus that comes bundled with Windows and is enabled by default, has been updated to detect any possible vulnerability exploitation. You need to install signatures version 1.367.719.0.
“Customers with Microsoft Defender Antivirus should turn-on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats. Customers of Microsoft Defender for Endpoint can enable attack surface reduction rule “BlockOfficeCreateProcessRule” that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy,” Microsoft notes.
 14 DAY TRIAL //
14 DAY TRIAL //