For around 48 hours between June 24 and 27, crooks used Facebook spam messages to distribute malware that hijacked user accounts to carry out operations such as giving likes and sharing unwanted content.
A security researcher from Russian security firm Kaspersky Lab discovered the campaign, which was spreading among Facebook accounts in the form of a spam message received from a friend that informed users about being mentioned in a comment.
Malware used a two-stage attack scenario
Accessing the link would start the first phase of the two-stage attack, which would secretly download a trojan on the user's computer.
During the second stage, this trojan would download and secretly install an extension in the user's Chrome browser, if found on the infected system.
The Chrome extension would wait until the user tried to access Facebook again, asking them to reauthenticate. At this point, the extension would log the user's Facebook username and password and send them to the crook's server.
The crook would then take advantage of these credentials and instruct these accounts to give likes and shares to desired content, while also spamming the infected account's friends to spread the malware further.
The crook behind this campaign was most likely selling Facebook likes and shares via their botnet of infected devices.
Campaign thwarted in less 48 hours thanks to attentive users
Because of the trojan's source code, this malware was only effective when users viewed the spam messages from Windows computers.
The Russian security firm said the malware tried to protect itself by blacklisting the homepages of several security software vendors.
"Two aspects of this attack stand out. Firstly, the delivery of the malware was extremely efficient, reaching thousands of users in only 48 hours. Secondly, the response from consumers and the media was almost as fast. Their reaction raised awareness of the campaign and drove prompt action and investigation by the providers concerned," stated Ido Naor, Senior Security Researcher, Global Research and Analysis Team, Kaspersky Lab.
Facebook engineers were alerted, and they moved on to block the techniques used by the malware to spread. Google has also removed the rogue extension from its Chrome Web Store.
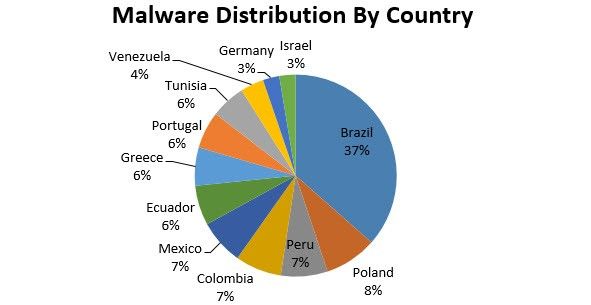
According to Kaspersky's data, the campaign made the most victims in countries such as Brazil, Poland, Peru, Colombia, Mexico, Ecuador, Greece, Portugal, Tunisia, Venezuela, Germany, and Israel.

 14 DAY TRIAL //
14 DAY TRIAL //