After yesterday Check Point security researchers discovered Brain Test, an Android app that installed malware on infected Android devices, today, ESET researchers are revealing Android/Mapin, a trojan that was distributed via six Android games as early as November 2013.
According to ESET, the following games were found to be infected with Android/Mapin: Hill climb racing the game, Plants vs zombies 2, Subway suffers, Traffic Racer, Temple Run 2 Zombies, and Super Hero Adventure.
Game developers were TopGame24h, TopGameHit and SHSH. According to ESET, when the games were pulled off the Play store, their developers uploaded them on the same day on alternative Android app markets. ESET also observed that the games reuploaded on other marketplaces still included the trojan.
Additionally, another developer, PRStudio (not prStudio), was also distributing games and applications with Android/Mapin from the same alternative Android marketplaces.
As with the previous ones, these games are trojanized clones of more famous games. In case you want to stay away from them, their names are Candy crush or Jewel crush, Racing rivals, Super maria journey, Zombie highway killer, Plants vs Zombies. A complete list is provided in the link at the end of this article.
Android/Mapin Modus Operandi
According to ESET researchers, the Mapin Android trojan managed to evade detection from Google's Bouncer security and scanning system by staying hidden for 24 hours.
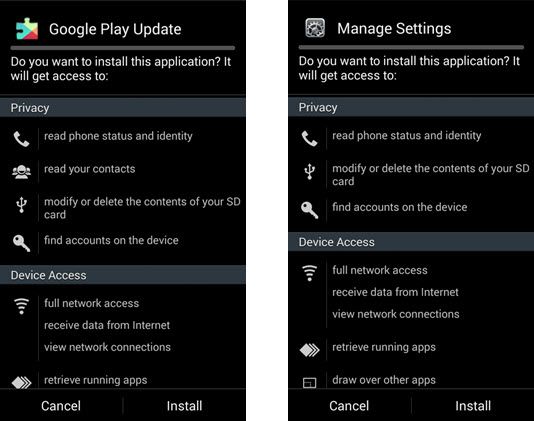
While other malware starts executing its malicious code at the moment the application is launched, Mapin waits for a day to pass and then pops up on the user's screen as a Google Play update or Manage Settings app.
Since the user most of the time won't even be interacting with the phone when this happens, they'll be fooled to think this is a regular update, and grant it the approval it needs. This is also helped by the fact that legitimate-looking icons and text are used, mimicking native Android settings screens.
Once allowed to install itself, the trojan registers the user's phone inside a botnet by sending identification data to a C&C server, and then moves on to request admin privileges using the same fake popup trick as used to install itself.
With admin privileges in hand, the malware then moves on to showing full-screen ads via AdMob every time the user's connectivity changes.
Stealthy code execution tactics allowed the trojan to remain undetected for 2 years
As ESET researchers detail, because the malware lies in hiding for 24 hours and only interacts with the user when their network state changes, Google's Bouncer detection system was unable to detect the malicious code being executed.
In some cases, ESET also reported that it took about three days since the malicious game was installed until the trojan managed to get admin privileges, which explains why Google's automated testing system wasn't able to detect for so many years.
For now, the malware is on a rampage among Indian users, ESET reporting that 73.58% of all Android/Mapin detections were recorded in India alone. The cyber-security firm is currently sporting a list of 20 Android games carrying this trojan in multiple Android marketplaces.

 14 DAY TRIAL //
14 DAY TRIAL //