Security company Promon has discovered a critical vulnerability affecting all Android versions, including Android 10, which can allow an attacker to obtain full access to a compromised device.
Baptized StrandHogg, the security flaw allows infected apps to pose as legitimate apps, and researchers explain that all top 500 most popular apps available on Android are currently at risk.
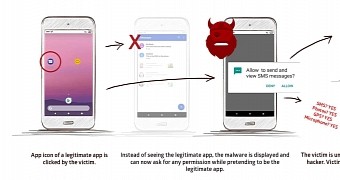
The vulnerability enables malicious apps to be disguised as legitimate ones by exploiting a bug in the Android multitasking engine. An infected app can ask for permissions on behalf of a legitimate app when users launch the multitasking interface, basically tricking targets into believing they are interacting with the legitimate one.
“This exploit is based on an Android control setting called ‘taskAffinity’ which allows any app – including malicious ones – to freely assume any identity in the multitasking system they desire,” Promon notes.
The request showing up on the screen can provide attackers with access to the camera, read and send messages, record phone conversations, get location and GPS information, steal the contact list and phone logs, and extract all files and photos stored on the compromised device.
“The attack can be designed to request permissions which would be natural for different targeted apps to request, in turn lowering suspicion from victims. Users are unaware that they are giving permission to the hacker and not the authentic app they believe they are using,” the Norwegian security company explains.
Vulnerability already being exploited in the wild
What’s worse is that Promon claims the vulnerability can be exploited without root access, and researchers from Lookout say they have already identified a total of 36 malicious apps whose purpose is to take advantage of StrandHogg.
Very important to know is that StrandHogg does not spread through applications published in the Google Play Store. However, it can use other infected apps that are already listed in the Play store to download the necessary payload that eventually exploits StrandHogg on a vulnerable device.
“We have tangible proof that attackers are exploiting StrandHogg in order to steal confidential information. The potential impact of this could be unprecedented in terms of scale and the amount of damage caused because most apps are vulnerable by default and all Android versions are affected,” Promon CTO Tom Lysemose Hansen says.
Promon has already reported the vulnerability to Google, but patches aren’t yet available. Google, however, removed the affected apps that could help drop StrandHogg on an Android device.
 14 DAY TRIAL //
14 DAY TRIAL //