Over the past three years, security researcher Ariel Sanchez from IOActive, has been auditing iOS mobile banking applications against a set of security-related issues.
His tests include searching for cleartext traffic, improperly validated SSL certificates, improper session handling, compiler protection checks, UIWebViews issues, problematic logging, binary file analysis, and searching for insecure data storage practices.
Apps still fail at proper HTTPS techniques
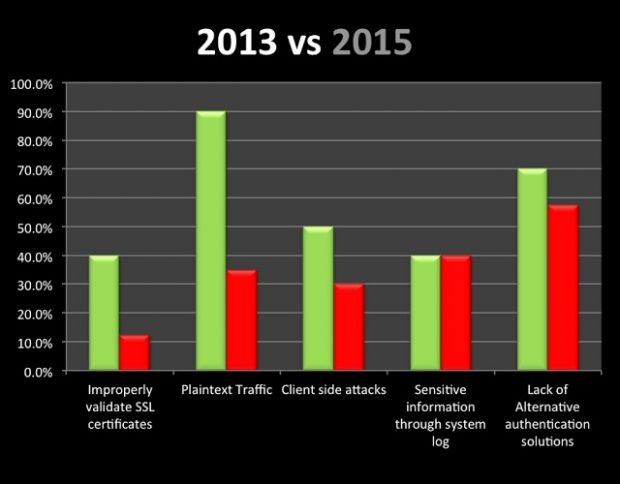
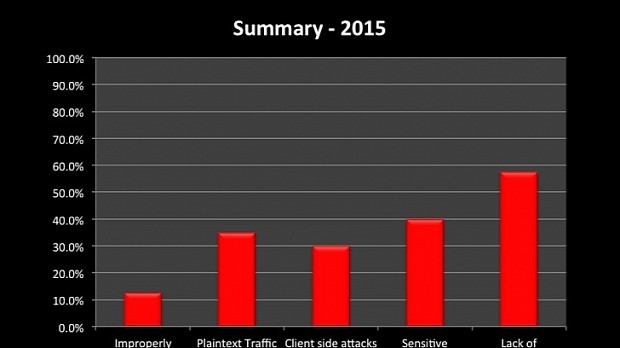
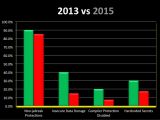
According to his most recent research, out of the 40 iOS mobile banking applications he tested, only 12.5% didn't validate their SSL certificates before initiating HTTPS connections, leaving users exposed to MitM (Man-in-the-Middle) attacks.
Additionally, 35% of the apps also contained links inside their content which were not handled via HTTPS, exposing users to arbitrary HTML and/or JavaScript code injections.
30% of the apps also didn't validate incoming data, which means that attackers can send it fake JS code and attack the user via the UIWebView component.
The good part is that more apps (40%) started providing alternative user authentication solutions. The bad part is that 42.5% of the apps also exposed some sort of private information via system or custom logs.
Developers still leave a lot of clues behind in their code
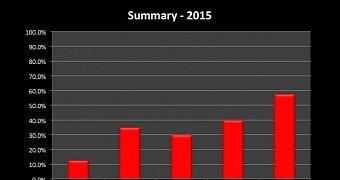
Moving on to binary and filesystem analysis, Mr. Sanchez also discovered that 7.5% of the apps still didn't have any type of compiler protection, allowing attackers to easily decompile them and access their code.
15% of the apps have jailbreak protection, and 17.5% of the apps stored some kind of hardcoded information in their binary files.
Furthermore, Mr. Sanchez still discovered 15% of apps still storing unencrypted and/or sensitive information on the phone, either as an SQLite database, or as a plaintext file.
All of these statistics were down from 2013, which is a good sign, but is still unsatisfactory after so many years of promoting proper coding and security techniques for iOS developers.
"While overall security has increased over the two-year period, it is not enough, and many apps remain vulnerable," concluded Mr. Sanchez.
 14 DAY TRIAL //
14 DAY TRIAL //