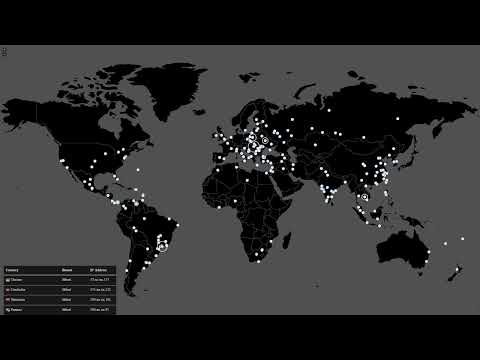
According to a recent analysis by security researchers MalwareTech and 2sec4u, initial estimations on the size of the Mirai botnet seem to be precise, with the botnet pulling in around 120,00 bots per day.
The numbers come from over 500 honeypot servers installed across the Internet by the two researchers, who configured the servers to imitate vulnerable IoT devices that had their telnet port open for external connections and used simplistic admin passwords.
These are the types of targets the Mirai trojan targets and infects, adding them to a botnet controlled by an attacker, which is rented and used to carry out DDoS attacks.
Mirai botnet confirmed to be comprised mainly of CCTV cameras
This botnet, even if not in the multi-million range that other botnets achieved during the 2000s, has grabbed headlines around the world after it was used to launch two of the biggest DDoS attacks known today, one of 620 Gbps against a journalist's website, and over 1 Tbps against a French ISP.
When the attacks took place, two weeks ago, the French ISP, OVH, estimated that the crook had used a botnet of over 145,000 infected IoT devices.
Similar reports from other security vendors also presented the same number and blamed vulnerable CCTV cameras as the main device type comprising the Mirai botnet.
This latter assessment is also true, according to MalwareTech, who confirmed initial rumors, and said that in most cases, the bots were CCTV devices running firmware made by Dahua Technologies, a Chinese-based vendor of white label CCTV and DVR hardware.
Get ready for tens of smaller Mirai clone botnets
MalwareTech's estimation of 120,000 bots for the Mirai botnet is similar to a Level 3 estimate from the end of August, when the company also noted the presence of the mammoth botnet, even if the Mirai malware hadn't been discovered by that point in time.
Nevertheless, the original Mirai botnet is slowly dying, after the author of the Mirai malware published the trojan's source code so other crooks could deploy it and create multiple Mirai clone botnets, and help him cover his tracks.
"Mirai, which was mostly ignored due to its unsophisticated telnet bruteforcing attacks, in the course of a week became the subject of worldwide media attention and multiple law enforcement investigation backed by multinational companies," MalwareTech explained.
As such, we might be seeing the last breath of this infamous botnet, but don't count Mirai out just yet. It's very likely that other threat actors will be deploying their own Mirai versions pretty soon, and based on the sizes of their botnets, might be launching similarly devastating DDoS attacks.
Below is a timelapse of Mirai bots coming to life and creating the DDoS botnet. For the real-time Mirai botnet map, you can go here.
 14 DAY TRIAL //
14 DAY TRIAL //