The impact of a data breach has more wide-reaching consequences than the service where it originated, security researchers from ThreatMatrix conclude in their most recent report.
Regardless of whether data breaches reach the public Internet or they're only in the possession of the crooks who stole them, if they contain cleartext or weakly hashed passwords, they will cause immediate damage.
The bad habit of reusing passwords for multiple accounts is not going away overnight, if ever. Crooks know this more than anybody else, and they're using this detail in their attacks.
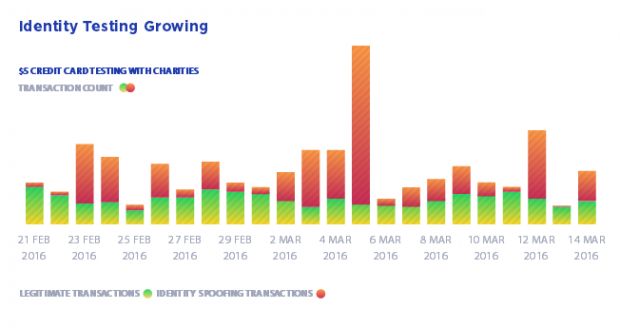
Data breaches lead to automated identity testing attacks
ThreatMatrix says that there was a rising trend during the first quarter of 2016 for automated identity testing attacks. Crooks use username & passwords leaked from data breaches to log into various other accounts, not just the ones that were exposed in the data breach.
"Once the fraudsters get a new list of user credentials from the dark web they launch a series of attacks targeting multiple sites to run massive credential testing sessions," ThreatMatrix explains. "Once they get a hit at any site, the fraudsters take this curated list of known combinations of passwords and logins to other sites to launch attacks at a slower velocity."
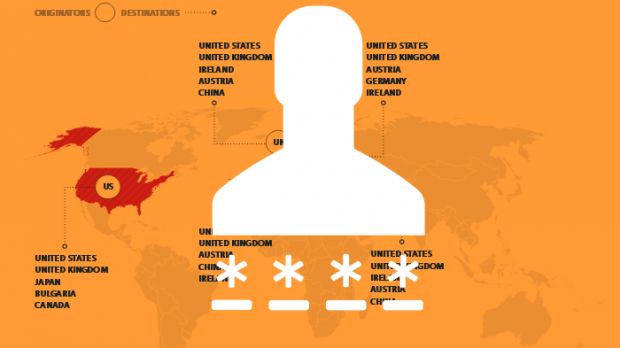
Once crooks get access to other websites, they use this access to commit fraud, especially on Web banking accounts. Using techniques like device spoofing, identity spoofing, IP spoofing, automated bots, malware, or Man-in-The-Browser (MiTB) attacks, not even two-factor authentication stands in the attacker's way.
Every two-bit crook seems to have a botnet these days
Besides a rise in identity testing attacks, ThreatMatrix also reports on other trends in the cyber-criminal underground.
First of all, criminals building and maintaining botnets are now a trend, and so are the attacks originating from them. Ranging from DDoS attacks to Web scanning, and from brute-force attacks to spamming, ThreatMatrix says it detected over 311 million botnet-originating attacks, of which over 264 million targeted e-commerce sites alone.
Additionally, the 200 percent growth in the number of mobile devices has also reflected in the cyber-criminal ecosystem, where mobile targeting malware and botnet attacks have also adapted.
These and many other details can be found in ThreatMetrix's Cybercrime Report Q1 2016.
 14 DAY TRIAL //
14 DAY TRIAL //