A study of 12 healthcare facilities, 2 healthcare data facilities, 2 active medical devices from one manufacturer, and 2 Web applications has revealed that hospitals have many glaring security holes that, if exploited by a determined attacker, could result in severe damage and even loss of human life.
This is the conclusion of a two-year study that was conducted by Independent Security Evaluators (ISE), a US security firm born out of a PhD program at the Johns Hopkins Information Security Institute in 2005.
The researchers studied medical facilities all across the US, commercially available devices and applications, but also in-house developed products.
Two-year research analyzed hospital security in depth
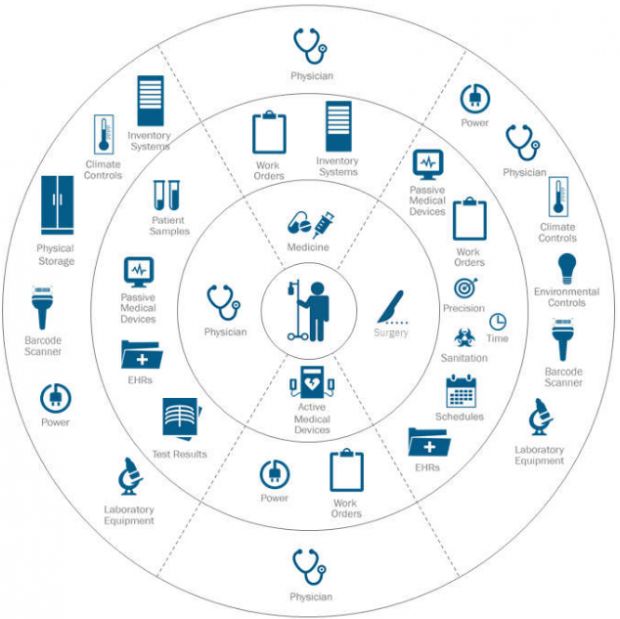
The research team looked at patient records, service availability, hospital finances, staff availability, regulatory interference, and many other factors to evaluate the security status of each hospital.
They also analyzed all the potential adversaries, not only hackers but also paparazzi, organized crime, terrorists, and even nation-state APT groups.
ISE researchers conducted staff interviews, inventory reviews, IT network audits, and policy reviews. After this, researchers put together attack scenarios, launched them against their targets, gathered results, and discussed the findings with hospitals and all affected parties so they could fix and mitigate similar threats.
All their results were also used to put together a blueprint of activities that can help the healthcare industry guard against basic attacks and improve security at their facilities.
Hacking medical devices can lead to loss of human lives
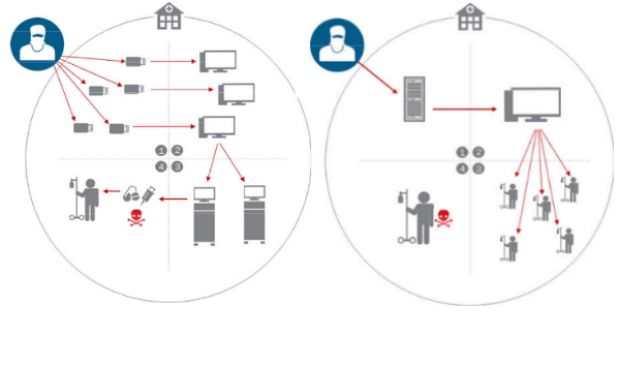
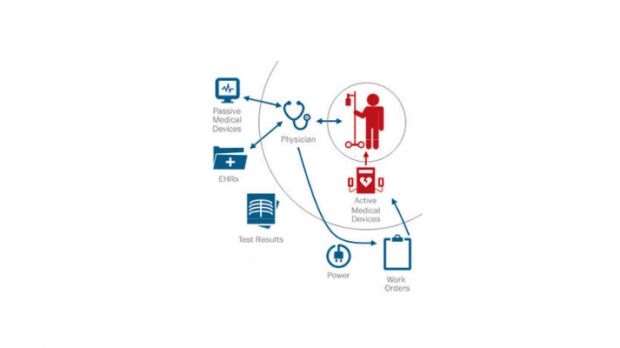
Some of the most devastating attacks they concocted were aimed at medical equipment that interacted directly with patients. By using the local network to infiltrate these devices, attackers would manage to alter and even stop treatment to patients.
Researchers say that, this way, attackers could target devices like insulin pumps, defibrillators, or X-ray machines.
Other attack routines include hackers altering hospital inventory records and sending the wrong medicine to patients, changing surgery schedules and delaying vital procedures, altering patient records to deny organ transfers, or removing critical medical information from a patient's history.
There are numerous other attack routines detailed in the report that a hacker could follow, and almost all have severe consequences on the patient's condition and even life.
Humans are the main factor behind these vulnerabilities
The blame for most of these attacks and vulnerabilities falls, as usually, on its operators, ranging from medical staff to IT administrators. Of course, device manufacturers and software providers aren't that innocent either.
ISE analysts discovered that many hospitals used insecure services, default device configurations, had no access control lists to prevent unauthorized access, used shared credentials, and often left their systems unpatched, despite the presence of newer, more secure firmware or software.
"As health care ecosystems increase in complexity and demands on their functionality grow, it is critical that security programs are positioned appropriately," said David Watson, ISE researcher. "Born out of intense research, the ISE blueprint provides the foundational framework to accomplish the right mission of securing patient health."
The entire 71-page ISE study, Securing Hospitals, is available online, and despite its bulky size, it is quite an interesting and enthralling read.
 14 DAY TRIAL //
14 DAY TRIAL //