Google researchers, alongside academics, have demonstrated that nothing is impossible by producing two different documents that have the same SHA-1 hash signatures. And that's a big deal.
Why, you ask? Well, it has everything to do with the fact that SHA-1 is used across the Internet. It's used for HTTPS certificates used to protect your browsing and in Git repositories. It is used to prove that data, whether it's emails, PDFs, website certificates, source code, and so on, has not been tampered with by hackers of any kind.
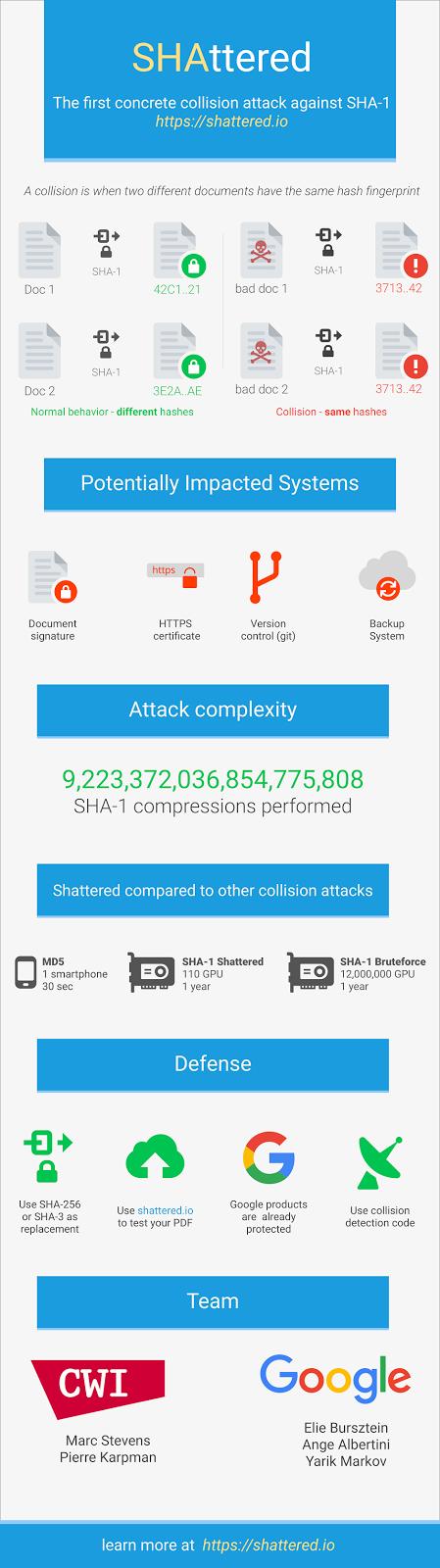
Well, Google has managed to prove that it is, in fact, possible to create a hash collision by altering a PDF without changing its SHA-1 hash value. This means that people could be tricked into thinking the altered document was actually the original one, which is worrisome.
"Today, 10 years after of SHA-1 was first introduced, we are announcing the first practical technique for generating a collision. This represents the culmination of two years of research that sprung from a collaboration between the CWI Institute in Amsterdam and Google," the company wrote in a blog post.
The purpose of this entire effort was to show the tech community that it is necessary to sunset SHA-1 usage. Google has advocated the deprecation of SHA-1 for many years, particularly when it comes to signing TLS certificates, specifically due to this type of problem. Chrome has been slowly phasing out the use of SHA-1 since 2014.
"We hope our practical attack on SHA-1 will cement that the protocol should no longer be considered secure," the team added, pushing the tech industry towards using a safer alternative such as SHA-256.
How did this happen?
It all started back in 2013 when Marc Stevens published a paper outlining a theoretical approach to creating an SHA-1 collision. Google and the rest of the team started creating a PDF prefix crafted to allow them to generate two documents with distinct visual contents, but with the same SHA-1 digest. By mixing Google's technical expertise and the cloud infrastructure, they managed to compute the collision, which is one of the largest computations ever completed.
When Google says this was a massive scale computation, it's not kidding. In fact, it offers some numbers. Nine quintillion SHA-1 computations had to be made, 6,500 years of CPU computations to complete the attack first phase, and 110 years of GPU computation to complete the second phase. These are extremely high numbers, and your regular attacker may not be able to complete it, but Google showed that an SHA-1 collision is possible, which should be enough.
"Following Google’s vulnerability disclosure policy, we will wait 90 days before releasing code that allows anyone to create a pair of PDFs that hash to the same SHA-1 sum given two distinct images with some pre-conditions. In order to prevent this attack from active use, we’ve added protections for Gmail and GSuite users that detects our PDF collision technique," the researchers said.

 14 DAY TRIAL //
14 DAY TRIAL //