The Gamarue botnet (also called Andromeda) has been seen in recent weeks using a different approach to distributing its malicious payloads, Stormshield security researcher Benkow reports.
The Gamarue botnet has been around since July 2011, when it was first sighted on the underground black market, advertised as a modular botnet that could spread all types of malware, from infostealers to banking trojans, and from ransomware to proxy malware.
Across time, this botnet has always evolved, being one of the most evasive threats, which authorities have failed to take down even to this day.
Researcher goes exploring Gamarue C&C server directories
As Benkow explains in his technical write-up, the people behind Gamarue have switched to delivering their payload from classic executables to the same technique employed by today's ransomware distributors, that of packing malicious JavaScript files inside ZIP attachments, which get executed automatically when the archive is unzipped.
But this is not what caught our eye as far as Benkow's research is concerned since this technique has become a trivial tactic today. You see, Benkow managed to discover the IP address of one of Gamarue's C&C servers, and after accessing this IP in his browser, he managed to guess some of the Web server's browseable directories.
Here, he discovered troves of information stolen from the botnet's victims. He found email credentials stolen from local Outlook installations, cookies extracted from local browsers, and even the login screen of the backend associated with the Pony infostealer used to steal the cookies and email credentials.
Researcher finds PCB admin panel used to manage Gamarue botnet
Because this particular malware campaign Benkow discovered was distributing the Pony infostealer, a spam malware package and the Hioles proxy malware, the researcher also went looking for the crooks' control panel for the proxy malware.
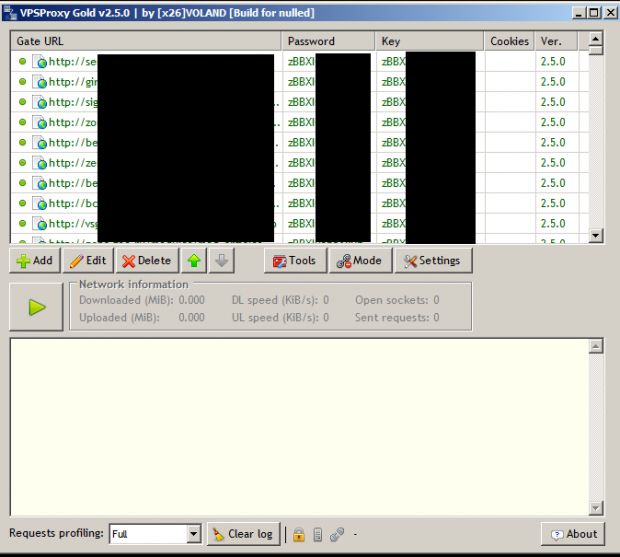
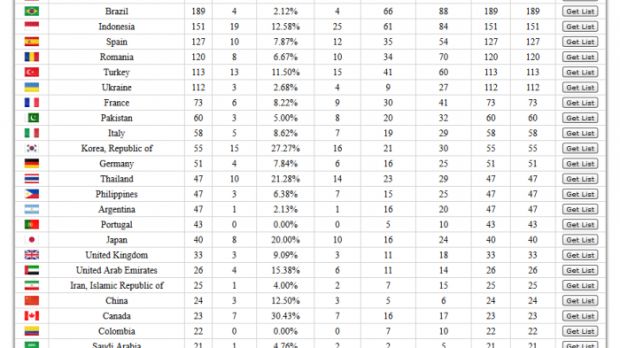
He eventually discovered a common tool used for such purposes, called ProxyCB or PCB. The researcher managed to break into the control panel, getting even more information about the Gamarue botnet's current victims, their location around the globe, and various other details.
Benkow's explorations continued, and in the C&C server's root directory, he discovered an HTML textarea that contained obfuscated source code. This later proved to be the malicious JavaScript code attached to the email spam that was sent to infect users.
Gamarue leverages WordPress sites to send out spam
His last discovery was of Gamarue's spam kit source code, the application used to send the spam email that contained the malicious WIP+JS as an attachment. As it turned out, this kit was intended for installation on hijacked CMSs, mostly WordPress, and used to send spam on the behalf of Gamarue's botnet operators.
What we loved most about Benkow's analysis was a recommandation he left at the end of his write-up, which is probably the best security advice of the past months.
"As a reminder, to protect the endpoint, you can change the default program to execute ‘.js’ files to execute Notepad.exe instead of wscript.exe. This prevents the script from being erroneously executed by a user." Which in turns prevents executing the malicious JavaScript file and avoids the workstation's contamination.
 14 DAY TRIAL //
14 DAY TRIAL //