An updated version of the FTCODE ransomware was spotted in the wild by researchers at Zscaler, and this time it looks like authors focused a little bit more on password stealing capabilities.
An analysis conducted by the ThreatLabZ team reveals that the malware specifically targets Italian-speaking Windows users, and the latest version, detected as 1117.1, employs a VBScript download method for a more sophisticated attack.
More specifically, attackers use emails to spread the ransomware to potential targets. The malicious emails include infected documents and VBScripts, which when executed run a PowerShell script that triggers the ransomware infection.
“The script first downloads a decoy image into the %temp% folder and opens it trying to trick users into believing that they simply received an image, but in the background, it downloads and runs the ransomware,” the security researchers explain.
Ransom note left in root folder
Unsurprisingly, the malware attempts to obtain persistence by creating a shortcut called windowsIndexingService.lnk in the Windows startup folder. Additionally, it creates a scheduled task called WindowsApplicationService. Both the shortcut and the scheduled task run the malicious WindowsIndexingService.vbs script.
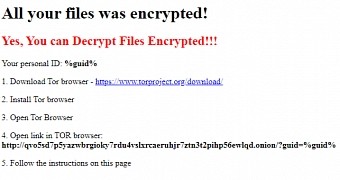
Once the device is infected, the ransomware encrypts a wide array of file formats and drops a ransom note called “READ_ME_NOW.htm” in the root folder.
“FTCODE generates a password using GUID and a random character set generated earlier. It uses Rijndael symmetric key encryption to encrypt the 40960 bytes of each of the above extension files. The initialization vector is based on 11 randomly generated characters,” the analysis reveals.
Users are instructed to download TOR browser and visit a link where they are required to pay for the decryption key that allows them to unlock their files.
In addition to encrypting files, the ransomware also steals credentials from the most popular browsers and email clients, including Internet Explorer, Mozilla Firefox, Mozilla Thunderbird, Google Chrome, and Microsoft Outlook. The ransomware can scan the default locations where these applications store credentials, extract the data, and then upload it to a C&C server.
 14 DAY TRIAL //
14 DAY TRIAL //