Trend Micro has discovered and helped thwart a malvertising campaign that was using free SSL certificates issued by the Let's Encrypt project to hide malicious traffic.
Malvertising, the tactic of using malicious code hidden in Web ads, is one of the easiest ways to distribute malware online. By sneakily inserting malicious ads on popular and legitimate websites, malware authors can redirect users to other websites, usually where a malware payload is delivered with the help of an exploit kit.
While security vendors are well aware of this sneaky trick and provide some protection through antivirus engines and various security APIs embedded in browsers, malvertisers can obfuscate their traffic by encrypting their communications.
Let's Encrypt helped everyone, including cybercriminals
For a long while, they usually purchased stolen SSL certificates via the black market, and deployed them in their malvertising campaigns. Fortunately for the rest of us, these certificates are eventually discovered, and revoked by their legitimate owners.
With the public beta launch of the Let's Encrypt project, an initiative backed by some of the Web's biggest companies, malvertisers have found that they don't even have to pay for SSL certificates anymore, and they can instead, request one for free.
Since any useful technology created for good can also be abused for evil, it took malvertisers around two weeks to deploy free Let's Encrypt certificates with their malicious campaigns, as cyber-security vendor and fellow Certificate Authority Trend Micro reports.
Let's Encrypt certs used to hide traffic for malicious ads
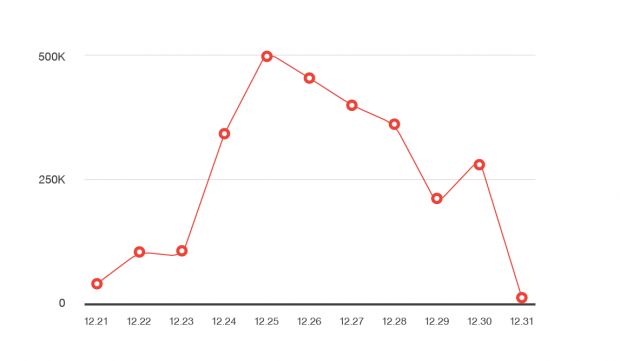
With Let's Encrypt entering public beta on December 3, Trend Micro researchers reported on the first malvertising campaign that used Let's Encrypt certs to hide its operations on December 21.
The campaign lasted until December 31 and affected users located mainly in Japan. People that were delivered malicious ads through this campaign, found themselves on a wild carousel, being taken to a page that hosted the Angler exploit kit, which infected them with the Vawtrack banking trojan.
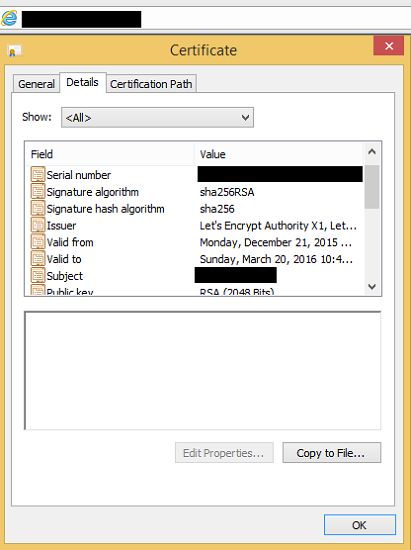
The malicious ads were hosted on a shadow domain (subdomain for a legitimate website, but pointing to a server controlled by the attackers), and all the traffic going to that domain was encrypted with a Let's encrypt cert.
There's a potential for abuse when it comes to Let's Encrypt certificates
Since Let’s Encrypt only checks the main domain against the Google Safe Browsing API, shadow domains like in this case are never detected, and the malvertising campaign authors can easily request and get approved for a Let's Encrypt certificate.
Trend Micro has notified both the Let's Encrypt project, and the legitimate domain's owner about the malvertising campaign.
With Let's Encrypt installed on 1,871 websites out of the most popular 1 million websites, the project is bound to see more abuses as webmasters (and cybercrooks) realize its true capabilities.
"Users should also be aware that a 'secure' site is not necessarily a safe site, and we also note that the best defense against exploit kits is still keeping software up-to-date to minimize the number of vulnerabilities that may be exploited," recommended Joseph Chen, fraud researcher at Trend Micro.

 14 DAY TRIAL //
14 DAY TRIAL //