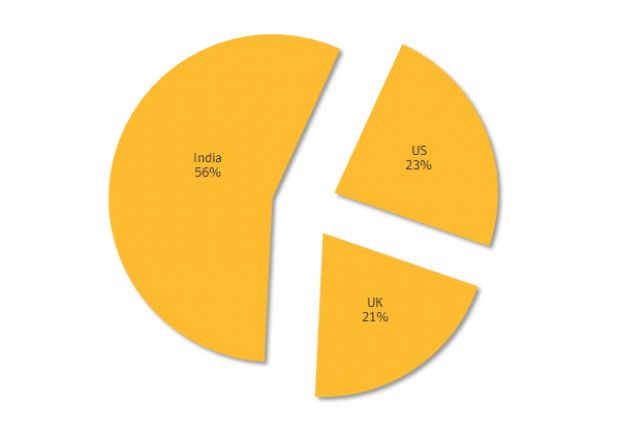
Several businesses in India, the US and the UK, have been the targets of cyber-criminals that have been infecting company computers with RATs (Remote Access Trojans) with the purpose of carrying out fraudulent financial transactions.
The campaign started at the beginning of 2015 and was first aimed at companies residing in India, and later the US. Towards the middle of 2015, the cyber-gang involved in this fraud campaign moved operations to the UK, where they continued to operate primarily.
The attacks are quite simple in their make-up and rely on classic social engineering tactics with the aim of tricking a company's employees into downloading and executing malware-infected files.
The group is using spear phishing email to spread the RATs
The criminal group followed the same scenario in all three territories they've attacked. It all starts with a spear phishing email, which the crooks send to a company's financial department, or representative if it's a smaller firm.
The email usually mimics regular correspondence received in any modern-day business from partners, collaborators or contractors, and has subject lines that mention invoices, orders, payments, quotations, and business inquiries. All of these are hard to distinguish from the regular mail a company would receive, even when the staff is specifically trained against phishing attacks.
The emails always include a file attachment, which is a ZIP file in most cases. Downloading and unzipping this file automatically starts the download and auto-installation of malware from the group's Web servers.
Crooks used the RAT to initiate fraudulent money transfers
Symantec reports that during the first stage of the campaign, carried out in India and the US, the group infected its targets with the Backdoor.Breut malware. When the group moved to the UK, they've changed the malware to Trojan.Nancrat.
Both are Remote Access Trojans, malware that allows remote access and control capabilities over infected computers.
Symantec claims that attackers were recording keystrokes, taking snapshots, and using the malware's backdoor feature to access the target's computer and later initiate money transfers to their own accounts.
"The majority of the messages are sent in the afternoon during Greenwich Mean Time (GMT) or morning during Eastern Standard Time (EST). This suggests that the attackers are based in Europe or the US," the Symantec Security Response insinuates.

 14 DAY TRIAL //
14 DAY TRIAL //