Security experts from Anomali Labs have revealed they've detected new versions of FrameworkPoS, one of the oldest PoS malware pieces on the market, in attacks against US-based small businesses.
According to telemetry data, the company says that the crooks managed to steal the Track 2 data from at least 300 credit cards, most of them from businesses in Honolulu, Hawaii, and the city of Chicago.
The researchers claim that this could be the sign of an upcoming large-scale FrameworkPoS, like the ones seen in late 2014 by G Data and late 2015 by Trustwave and FireEye.
FrameworkPoS is also one of the two malware families used in the infamous FIN6 operation detected last year, during which crooks stole 20 million credit card details from over 2,000 PoS systems, creating damages of $400 million (€355 million).
The scale at which the crooks operate is small for now, but researchers note that they expect the campaign to pick up in the upcoming future.
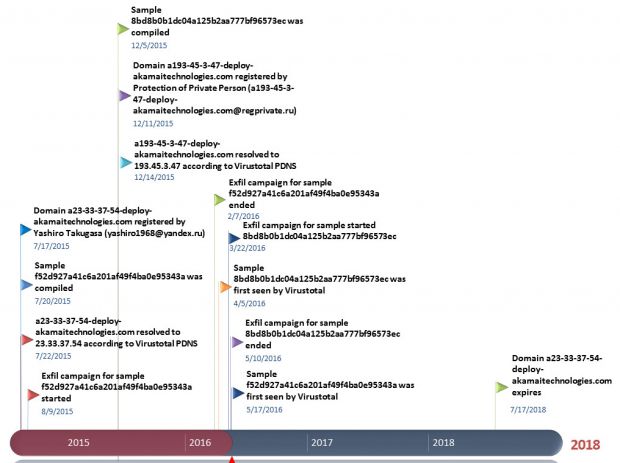
Anomali also points out that the group behind this recent wave of connections was registering domain names employed for the command centers in use today as early as July 17, 2015. Even if there's proof that the group has been active for a long time, there's no evidence to link them to the previous campaigns.
Below is a graph showing how the crooks registered and used their domains in the past months.

 14 DAY TRIAL //
14 DAY TRIAL //