A phishing campaign using multiple samples of the CARROTBAT dropper and more than one payload to attack Korean cryptocurrency related targets is doing the rounds according to Palo Alto's Unit 42 research team.
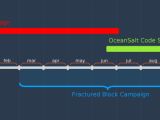
The Fractured Block campaign started back in March 2018, and it uses all the CARROTBAT samples observed in the wild up to this point.
According to Unit 42, CARROTBAT "is a dropper that allows an attacker to drop and open an embedded decoy file, followed by the execution of a command that will download and run a payload on the targeted machine."
Additionally, once the decoy document dropped by CARROTBAT on the targeted machine is opened, an obfuscated command will be launched in an attempt to download and execute a remote executable using the Windows built-in certutil utility.
As detailed in Unit 42's analysis, the Fractured Block campaign makes use of 29 different CARROTBAT versions which are employed to drop various malware payloads on the compromised systems.
The same threat actor might be behind CARROTBAT, OceanSalt, SYSCON, and KONNI activity
Moreover, the payloads range from SYSCON RAT samples that use FTP to communicate with its command-and-control (C2) servers, to OceanSalt malware samples known to have been used by the Comment Crew (aka APT1) threat group to attack targets from North America.
Unit 42 also states that the 11 decoy documents used by the phishing campaign use various subjects designed to lure victims into launching the CARROTBAT dropper on their machine, spanning from business cards to major political events around the date of the attacks.
In addition, the researchers noticed during their analysis of the Fractured Block phishing campaign that the CARROTBAT and KONNI malware families feature an infrastructure overlap, with KONNI also known to focus on South Asian targets in the past.
"Finding CARROTBAT provided an important lynchpin in identifying Fractured Block Campaign activity. Using CARROTBAT, we were able to find related OceanSalt, SYSCON and KONNI activity," concluded Unit 42. "The various overlaps encountered are notable, and it is our suspicion that this threat activity may all belong to the same threat actor."

 14 DAY TRIAL //
14 DAY TRIAL //