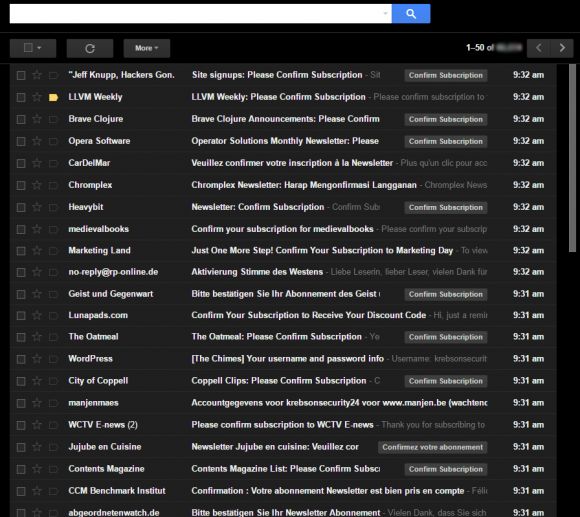
A massive email-based attack occurred over the weekend of August 13 and 14, which resulted in the flooding of 100+ email inboxes for various government accounts, and other smaller targets.
The attacks, called "email bombs," took place because careless website owners and mailing list managers had not secured their web forms against automated bots.
An unknown group had compiled a list of unsecured web forms and mailing lists and subscribed official government email addresses to these lists.
Mailing lists and WordPress sites abused in the attack
Attackers used bots to take a target's email address and enter it into a contact form, account registration form, or mailing list that generated an automated response in the form of confirmation or notification email.
On Monday morning, government officials or other affected parties who opened their email clients found hundreds or thousands of email subscription confirmations in their inboxes.
Because these emails came from previously legitimate sources, not all were marked as spam in the beginning. Nevertheless, as the attack surged over the weekend, Spamhaus, an organization that manages a blacklist of IP addresses banned for spamming, took notice of the incident.
Email bomb attack generated around 1,000 spam emails per minute
Spamhaus says it was forced to add the IPs of legitimate companies and email service providers to its blacklist because of the ongoing attack.
The company claims the attack reached never-before-seen metrics. Spamhaus says one company saw nine email addresses signed up over 9,000 times over the course of two weeks, which generated 81,000 confirmation emails to those inboxes.
The automated bots produced around 1,000 confirmation emails per minute, spread to all 100+ targeted email addresses. One of the extreme cases is one email provider who saw 22,000 sign-ups from 3,000 different sites, in a rapid succession, resulting in 100 messages per minute to some specific email addresses.
Besides government email addresses, attackers also targeted infosec journalist Brian Krebs, and even Spamhaus inboxes, after the company started blacklisting some of the IPs belonging to legitimate websites abused by the attackers. A photo of Brian Krebs' Gmail inbox showing all the resulted email junk is embedded below.
Careless webmasters are to blame
Spamhaus puts the blame for the attack solely on the shoulders of website and mailing list operators who have not secured their public web forms against bots.
"These signups were made possible by the fact that many web forms use Single Opt-In (SOI) and accept all subscriptions without any verification, though in this case even using Confirmed Opt-In (COI) didn't help much because the volume of confirmation emails alone was enough to cause a substantial problem," Lys Maltice of Spamhaus explains. "In fact, many of the lists that were victimised had already been using COI."
Maltice also revealed that around half of all the email bomb spam came from WordPress sites that allowed user registrations. These sites failed to protect the account registration page with a CAPTCHA, which the crooks leveraged to generate an account creation email that ended up in someone's inbox.
Spamhaus advises webmasters to deploy CAPTCHA fields with their forms and recommends Google's reCAPTCHA service as a viable solution.
The company also claims that this attack looked like a small test, possibly for a Mail-bombing as a Service (MaaS) offering on underground cyber-crime forums.

 14 DAY TRIAL //
14 DAY TRIAL //