Operators of the Dridex banking trojan are experimenting with a new technique of delivering spam to their victims, according to independent security researcher MalwareTech.
The researcher has recently spotted a spam wave coming from legitimate but compromised websites, which the crooks were abusing to send spam to victims, most predominantly to users living in the UK.
Crooks experimenting with non-Necurs delivery channels
There are two new techniques employed by the Dridex crew in this campaign. The first is the use of compromised servers to send spam. Previously, the Dridex gang had relied on the Necurs botnet, a network of compromised computers.
Because crooks used such a novel tactic, it took security firms some time to discover the new campaign and properly mark it as spam.
The second technique is in the email themselves. "The malicious rtf (Word Document) has been encrypted with a password given in the email," MalwareTech noted. "This would prevent most automated systems from extracting and scanning the attachment for malicious code, as most aren’t able to handle password extraction or document decryption."
New spam wave hard to detect by malware scanners
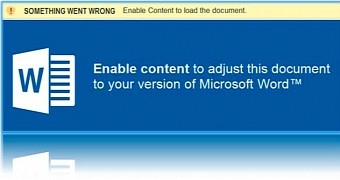
While security software may have difficulties analyzing and detecting the malicious files sent in this new campaign, users don't have any problems in finding the password and using it to open the RTF file. Once users open these files, they are asked to enable macro script execution with a clever message.
When they execute, these macro scripts download and install the Dridex Loader, which is different from previous campaigns as well. MalwareTech says the Dridex Loader starts a command-line interface and pings one of Google's free DNS servers 250 times before doing anything remotely malicious.
"Overall this campaign does seem to pack a bit more of a punch tha[n] the ones we’re used to, possibly with the intention of infect[ing] corporate systems with more advanced threat protection rather than home users," it states.
Previously, security researchers have discovered Dridex campaigns targeting smaller countries and found the first signs of the trojan preparing to target crypto-currency wallets.
Dridex is back targeting the UK (and others) with botnet 302. Spam is coming from mailer scripts rather than a botnet to bypass spamfilters. — MalwareTech (@MalwareTechBlog) September 27, 2016
 14 DAY TRIAL //
14 DAY TRIAL //