A security researcher named Stefano Vettorazzi has discovered a method of using Heroku's own social buttons against the company, thus taking over user accounts from their rightful owners.
Heroku, an app hosting platform that's quite popular with Ruby and Node.js devs, comes with a social button called "Deploy on Heroku."
Developers can add this button to their source code repositories, and you can usually find it on many project pages on GitHub, GitLab, Bitbucket, and so on.
Heroku users who click this button will clone and install the project as an app into their Heroku account, allowing them to set it up within seconds on their servers and have it running in no-time.
Pwning via project logos
For this action, Heroku uses the app.json file stored in the source code repo. This file works as a general config and holds many parameters, which the researcher said were protected from tampering, except one.
Vettorazzi discovered that the user could set an image URL in the app.json file that would be used for the project's logo in the Heroku account management dashboard.
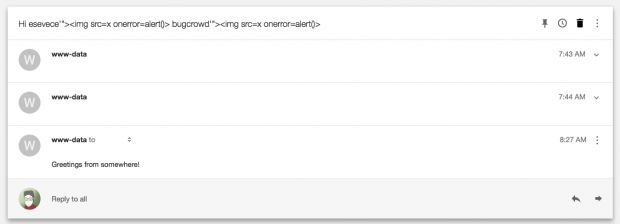
Using a leak of the "referer" data in the HTTP request when users press the Deploy button, along with an unprotected parameter in Heroku's OAuth implementation, he was able to modify the project deployment process so as to load malicious URLs instead of the project logo URL.
Heroku OAuth also leaked a global API access token
The attacker would only have to modify the content of that malicious URL that gets loaded instead of the project logo to control what kind of attack he wants to carry out. But the researcher says this didn't allow him to do that much. This changed when he realized he had an ace in hand.
The ace was the unprotected OAuth parameter mentioned above, which disclosed a Heroku access token, as Vettorazzi himself explains:
“ The value of this parameter is sent to an endpoint which doesn’t have CSRF protection and returns a JSON response including an 'access_token' with 'global' scope. This 'global' scope allows you to do anything with the account using the API. ”
This API access token helped the researcher carry out the initial attack by creating malicious projects and loading the malicious URL instead of the logo URL, but Vettorazzi discovered that it would also allow him to escalate his access.Using this access token, Vettorazzi was able to modify an account's password and take over a test account supplied by a member of Bugcrowd, the platform through which Heroku handles bug reports.
Heroku has fixed the issue, but a general warning is still valid, so developers won't deploy unverified projects to their Heroku accounts.

 14 DAY TRIAL //
14 DAY TRIAL //