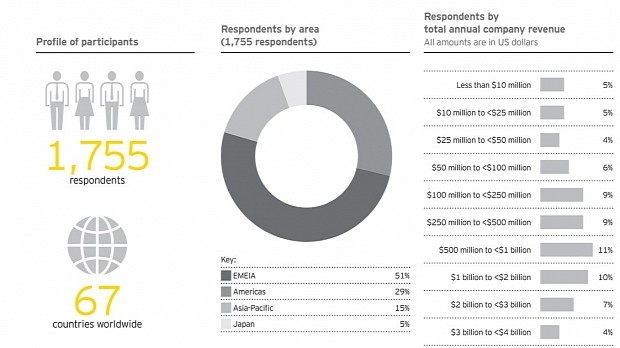
1,755 respondents from 67 countries and 25 industry sectors consider criminal syndicates the main source of cyberattacks during the past year, EY's Global Information Security Survey reveals.
With information gathered from top level management positions like CIOs, CISOs, and C-level executives, the survey provides a glimpse into the security departments of some companies around the globe.
With the number of cyberattacks and cyberthreats growing in recent years, in 2015, 88% of survey respondents say they don't believe their current information security levels are strong enough to meet their organization's needs for privacy and security.
Most managers, when asked to point to which threats and vulnerabilities have most increased during the past 12 months, have stressed that what they fear most is the presence of outdated information security controls and architectures, insider threats, phishing, and malware attacks.
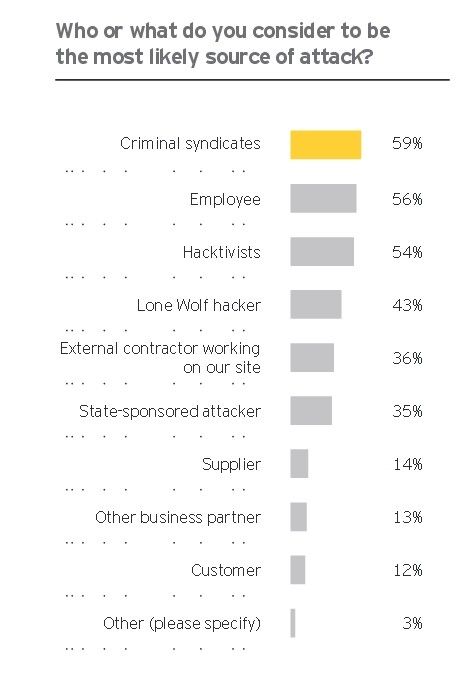
59% of the managers also add they suspect organized criminal groups behind these threats and vulnerabilities while only 56% claim they believe employees capable of such actions, and 54% place the blame on hacktivism groups.
Fewer managers fear the lone-wolf type of hackers (43%), external contractors (36%), and state-sponsored attackers (35%). Even fewer suspect suppliers (14%), business partners (13%), or customers (12%).
Awareness of criminal syndicates has gone up in the last year
Compared to 2014, suspicion of attacks carried out by criminal groups has gone up from 53% to 59%, as it did for attacks carried out by hacktivist groups (from 46% to 54%), and state-sponsored groups (from 27% to 35%).
"Cyber criminals can spend months inside your organization, finding information that they will store for a future attack or piecing information together that will get them to the prize they are after, they will also create measures to protect themselves from your detection," says EY.
"Sometimes they create diversionary tactics to draw your attention away from what they are doing and where they have succeeded. Often the criminals will keep the stolen information and not use it for a while - at other times, they will share it among the cybercriminal community (perhaps for a fee), spreading the direct threats to you even further," EY also notes.
For more details on the subject, along with information on a wide variety of security-related topics, check out EY's Global Information Security Survey.
 14 DAY TRIAL //
14 DAY TRIAL //