Multiple high-profile U.S. retail, restaurant, and grocery chains have been targeted by massive malicious email campaigns that peddled the Remote Manipulator System (RMS) tool and the FlawedAmmyy remote access trojan (RAT) since November 15.
"We attributed these campaigns to TA505, the actor behind the largest Dridex and Locky ransomware campaigns of the last two years and more recently associated with distribution of remote access Trojans (RATs) and downloaders," according to Proofpoint.
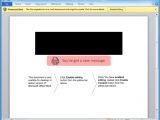
The researchers also observed that the email attachments included with the malicious emails distributed by the TA505 campaigns were personalized with the targeted company's logo to make them more credible and, hence, more efficient.
Moreover, targeting marks from the retail industry during the hectic holiday shipping season with the help of custom malicious emails shows yet again the TA505's predisposition to adapt their attacks to follow the money trail.
Proofpoint also stated that "When this group changes tactics, it tends to correspond to broader shifts and, throughout the year, we have seen both TA505 and a number of other actors focus on downloaders, RATs, information stealers, and banking Trojans, often in smaller, more targeted campaigns."
During the December 3 malspam campaign, the threat actor delivered tens of thousands of emails with every targeted organization receiving their own variant of malicious email, a never before seen TA505 technique.
TA505 targets the increased activity in the retail system during the holiday season
In one case, the email displaying a company logo to make it a more effective lure contained a Word document attachment which used macros that downloaded an MSI file installing the remote administration RMS tool.
"Threat actors follow the money and, with dropping cryptocurrency values, the return on investment in better targeting, improved social engineering, and management of persistent infections now seems to be greater than that for large “smash and grab” ransomware campaigns," concluded Proofpoint.
The TA505 threat group was also behind the modular Remote Access Trojan dubbed tRat, as well as for the 2014 Dridex and the Locky campaigns.
TA505 also used other malware payloads, from Shifu and The Trick banking trojan and the Necurs botnet to the even more dangerous Philadelphia, Jaff, Bart, and GlobeImposter ransomware strains.
All of the above malware strains were distributed at some point in time with the help of vast spam campaigns designed to compromise as many targets as possible with the smallest amount of effort possible.

 14 DAY TRIAL //
14 DAY TRIAL //