A Chinese cyber-espionage group has been keeping a watchful eye on China's minorities, especially on prominent activists and organizations, Palo Alto Networks reports.
The group, named Scarlet Mimic, has been operating for the past four years and has built its own spying tools for this particular task.
Most of the attacks are aimed at the Uyghur and Tibetan minorities, both of which have been at odds with the Chinese leadership since the Communist Party took the country's reins after World War II.
Besides minorities, Palo Alto researchers mention that Scarlet Mimic attacks were also seen against government organizations in Russia and India, organizations tasked with tracking activist and terrorist activities abroad.
"We do not have evidence directly linking these attacks to a government source," said Palo Alto's researchers, "but the information derived from these activities supports an assessment that a group or groups with motivations similar to the stated position of the Chinese government in relation to these targets is involved."
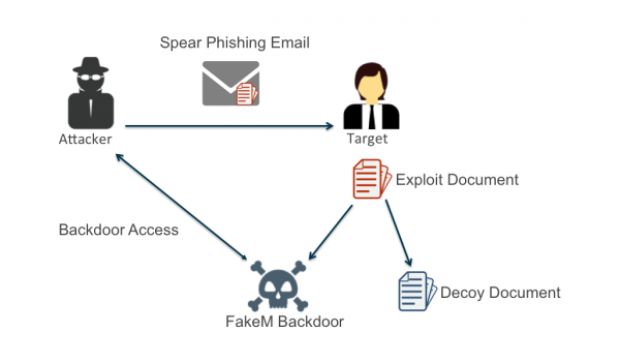
Scarlet Mimic's main weapon is the FakeM backdoor
In their attacks, most of the times, Scarlet Mimic deployed a backdoor trojan targeting Windows, called FakeM, first discovered by Trend Micro circa 2013.
This backdoor made waves when it was first discovered because it mimicked Yahoo and Facebook Messenger for its C&C communications protocol.
By analyzing the most recent attacks, which were all linked by a common C&C server, security researchers also discovered variants of the FakeM backdoor also targeting Mac OS X and Android devices, meaning the group has kept its tools updated to the latest trends in the tech world.
The group is still using spear-phishing and watering hole attacks
What hasn't changed is the group's tactics for infecting users, which remained the same old spear-phishing emails and watering hole attacks (malware served to victims via compromised legitimate websites).
One ingenious trick the group concocted was the use of RTL (Right-To-Left) text in the file names so that they could hide the file's true extension. This made it more likely that their malware was downloaded and then executed (installed) on the targets' computers.
Palo Alto says the most recent Scarlet Mimic attacks happened in 2015 and targeted the Muslim population living in China. Additionally, the group also kept an eye on organizations actively criticizing both the Russian Government and President Putin.
All of these details mean the group is very well funded, has clear targets, and doesn't necessarily go after easy-to-monetize data, being more focused on extracting political information from their victims.

 14 DAY TRIAL //
14 DAY TRIAL //