VDR (Voyage Data Recorders) devices installed on ships that often make international voyages are susceptible to cyber-attacks that may compromise them and allow attackers to spy on the vessel's movements or tamper with recorded data.
VDRs are for ships what black boxes are for planes. They record the ship's movements, the commands received from the crew, engine behavior, and a whole lot of data from sensors spread around the boat.
They are important not only for the ship's owners, allowing them to keep track of the vessel's whereabouts, but also for authorities in case of official investigations.
A short history of VDR hacking
Research carried out by IOActive reveals that these devices can be tampered with by hackers who know what to look for. Since the VDR is an embedded Linux box, it is vulnerable to a broad range of cyber-attacks these systems are usually exposed to. On top of this, the VDR is not tamper-proof like airplane black boxes, and some crew members have access to it and may compromise the data if they ever had a reason to.
In the past, there were two incidents that involved VDRs. In February 2012, two Indian fishermen were shot after boarding an Italian ship. The crew justified its actions by saying that they thought the two were pirates, but during the investigation, authorities found out that data from the VDR was mysteriously corrupted, and they could not access crew communications and other information stored on the device around the conflict.
A second incident occurred in March 2012, when a Singapore ship hit and damaged another boat, and then fled to the open sea. Three men were killed, and one was lost at sea but later rescued. During the subsequent investigation, authorities discovered that "someone" inserted a pen drive in the VDR, infecting it with malware and corrupting the data.
VDRs deemed woefully insecure
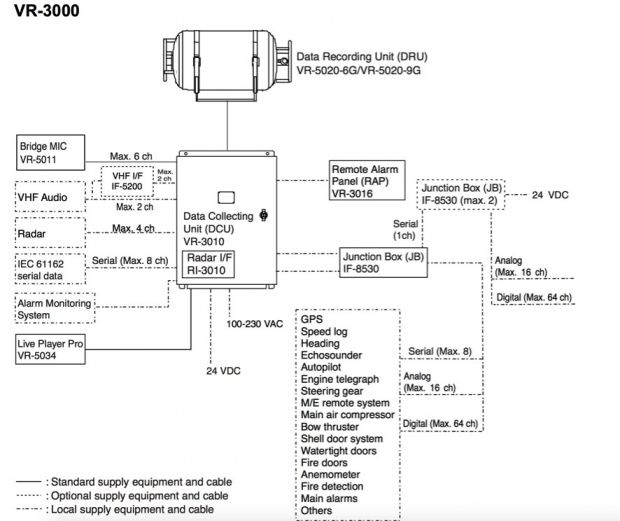
IOActive researchers analyzed a VDR used in one of the incidents, produced by hardware maker Furuno - the VR-3000 model. Their research revealed that the VDR is vulnerable both on the hardware and the software side.
First off, the VDR comes with open ports. While they were put there to aid authorities in extracting data from the VDR in case of an investigation, common sense says that these ports can also be accessed by the crew, if they desire to compromise data, which obviously happened.
While they need special cables to access the device, an IEEE 1394 cable (4P-6P), these can be easily purchased from specialized stores.
On the software side of things, IOActive found multiple buffer overflow vulnerabilities, remote command execution flaws, lack of any strong encryption, and stated that the device's firmware could be updated during a cyber-attack.
An attacker would need physical access to the device and Furano's special software, but the IOActive researchers managed to obtain a copy of the special Furano software without going through official channels during their research, so technically, it is also possible for others to do so as well.
Successful exploitation of the flaws discovered by IOActive would allow attackers to compromise not only the VDR's DCU (Data Collecting Unit) but also its DRU (Data Recording Unit), where the data is actually recorded on the DCU's hard-drives.
Compromising the VDR recording unit would allow attackers to spy on the ship's movements by collecting radar information and GPS locations. Additionally, cabin conversations can also be stolen or listened to in real time via the VDR.
IOActive notified Furuno of the vulnerabilities, and the company committed to issuing patches "somewhere in 2015." As of December 9, IOActive was not aware of any Furuno patches.

 14 DAY TRIAL //
14 DAY TRIAL //