Crooks who sold illegal products on Dark Web marketplaces failed to strip EXIF data from their photos which, in a large number of scanned photos, contained clues about their geographical location.
This is the result of a study carried out by Harvard students Paul Lisker and Michael Rose, who created special software to scan images saved in the Black-Market Archives, a project that copies content from illegal Dark Web marketplaces for historical purposes.
The Black-Market Archives offered the two data from 83 different portals and 40 forums associated with these marketplaces, from 2013 to 2015. In total, there were 44 million files or 1.5 TB.
Researchers scanned over 7.5 million images
Using a collection of Bash and Python scripts, the two researchers analyzed this archive and separated only the images.
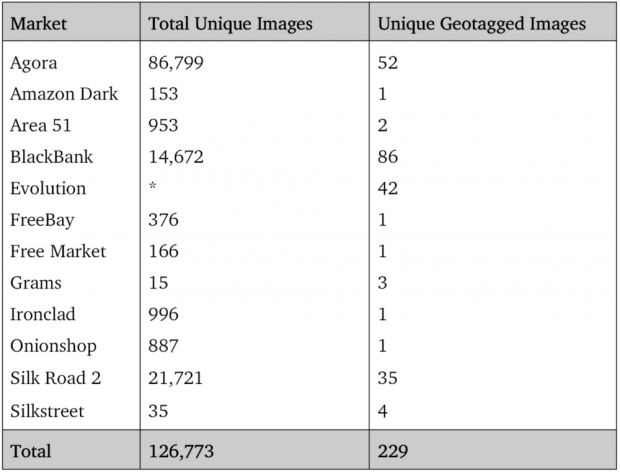
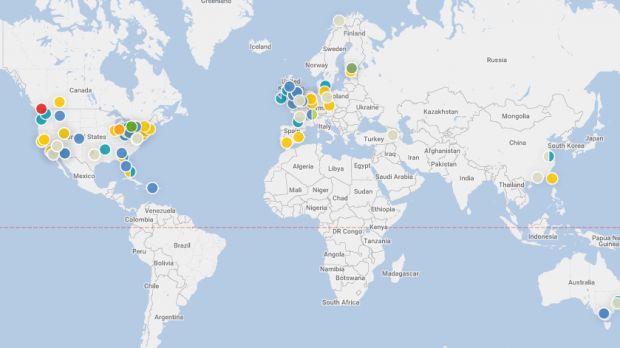
They then scanned these 7,522,284 photos (223,471 after removing duplicates) and discovered 2,276 total geotagged images. After removing duplicates from the final results, researchers were left with 229 images for which crooks forgot to strip metadata, leaving intact not only the make and model of the camera with which the image was taken but also accurate GPS coordinates.
After cross-referencing the images against all marketplaces, researchers discovered that most of these geo-tagged photos were posted multiple times across different marketplaces and forums, which explained the large number of duplicates.
This finding also reveals that a few Dark Web sellers lacked any understanding of OpSec, with the same offenders continuing to post geo-tagged images time after time.
Some marketplaces implemented EXIF strippers
Furthermore, researchers also found something interesting in the geo-tagged images uploaded on Agora, one of the Dark Web marketplaces.
They found 963 geo-tagged images between January 1, 2014, through March 18, but none after that. Researchers say the sudden cut-off most likely came from server-side countermeasures implemented by Agora's admins.
"It was common in many cases to observe sites, typically residential, surrounded by 5–10 tagged images separated by a few meters," the researchers wrote. "This suggests the behavior of sellers who are careless on a regular basis, rather than the occasional forgetfulness of not stripping data or purposeful manipulation."
Facebook does it better!
But the two researchers point to failures on both sides. Both sellers, for failing to remove their EXIF tags, and Dark Web admins, for not automating a process that stripped a photo's metadata for their users.
As an example, the two Harvard students lauded Facebook for hiding EXIF data for its images when viewed by users, but keeping it in its database for further analysis.
Failure to properly set up a TOR-based web server is what helped the FBI arrest the administrators of Playpen, the biggest child pornography portal on the Dark Web. In that case, a server misconfiguration leaked its real IP address, which agents used to track down the web hoster, and then the person who rented the server.
 14 DAY TRIAL //
14 DAY TRIAL //