Canonical this week rolled out an update for the Snapd daemon in order to resolve a vulnerability called Dirty Sock which allowed hackers to gain root access on Ubuntu and other Linux distros.
The security flaw, tracked as CVE-2019-7304, was discovered by researcher Chris Moberly of The Missing Link, who explained in a technical analysis that Snapd versions 2.28 through 2.37 are all affected.
Moberly says that the local privilege escalation vulnerability was reported to Canonical, the makers of both Ubuntu and Snapd, in late January. The patch was published this week by Canonical as Snapd 2.37.1, alongside security updates for Ubuntu and other Linux distros, including Fedora, Arch Linux, and Debian.
The researcher notes that the Snapd daemon, which is being used on modern Linux operating system to distribute apps alongside all the prerequisites for more seamless installation, comes with a bug in the API that allows any local user to gain root access.
Patches already available
This means that while the systems aren’t exposed to remote attacks, any potential hacker who gains control of the Linux machine can then obtain root privileges by exploiting this bug. The exploit can even be included in crafted snaps which can compromise targets when launched.
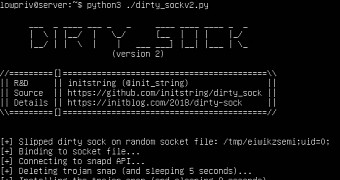
“snapd serves up a REST API attached to a local UNIX_AF socket. Access control to restricted API functions is accomplished by querying the UID associated with any connections made to that socket,” the researcher notes.
“User-controlled socket peer data can be affected to overwrite a UID variable during string parsing in a for-loop. This allows any user to access any API function. With access to the API, there are multiple methods to obtain root.”
In his technical write-up, Moberly says the exploit was successful on Ubuntu 18.10, but older versions are vulnerable as well. He also confirmed on Twitter that all systems using Snapd are vulnerable.
Users are now recommended to update to the latest version of Snapd and to also install the most recent security patches for their Linux distributions. While the vulnerability has already been fixed, older versions remain exposed, so it’s critical for all devices to be patched as soon as possible.
 14 DAY TRIAL //
14 DAY TRIAL //