In the past six months, the Buhtrap cyber criminal group has changed its mode of operation and has started robbing Russian banks, instead of their clients, Russian security firm IB-Group reports.
Buhtrap first surfaced in the summer of 2014. A year later, ESET published an exposé of the group's activities and tactics, revealing how the hackers used sophisticated malware combined with simplistic infection techniques to compromise the financial departments of businesses in Russia and Ukraine.
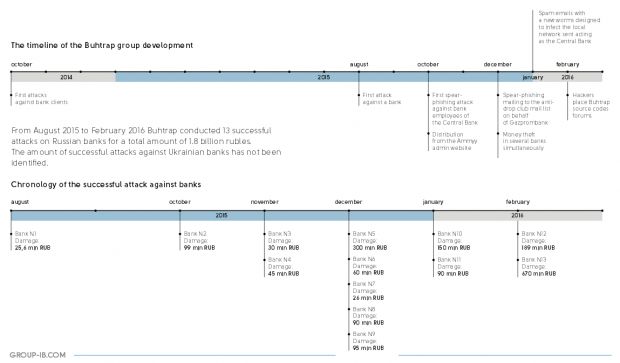
As IB-Group reveals in its latest report, since August 2015, the Buhtrap gang has changed targets completely and has taken aim at 13 Russian banks in a series of coordinated cyber-attacks.
The methods employed by the groups are almost the same as their previous tactics, relying on spear-phishing emails sent to bank personnel.
Buhtrap infects bank computers with spyware
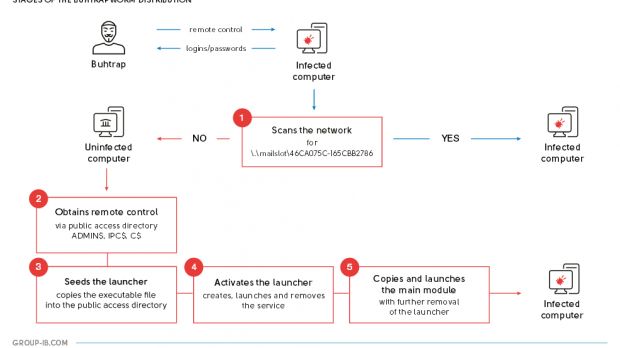
These emails contain a weaponized Word document that leverages a well-known vulnerability to facilitate the infection with spyware that opens a backdoor on the infected PC, logging keystrokes, taking desktop screenshots, stealing clipboard data, and even installing other malware.
Once the group gains control of a key bank workstation with access to financial operations (AWS CBC software must be installed), it would replace legitimate transactions with ones that redirect money to its own accounts.
From August 2015 to February 2016, IB-Group says the hackers hit 13 Russian banks and stole 1.8 billion rubles ($25.7 million). Their biggest heist was of 600 million rubles ($8.8 million) while the smallest amount was of 25.6 million rubles ($0.37 million).
Authorities managed to stop several heists, which would have pocketed the crooks another 1 billion rubles ($14.76 million). IB-Group says it does not have data on the group's activities in Ukraine, but there are signs that bank cyber-heists took place in the neighboring country as well.
Buhtrap malware source code leaked online
At this moment, the situation looks bleak because, on February 5, one of Buhtrap's members seems to have intentionally leaked the malware's source code on underground hacking forums.
The Buhtrap member said he was in charge of creating the group's malware and decided to leak its source code because he didn't receive payment for his work.
If we have learned something from malware source code leaks, it's that, as soon as it happens, other criminal groups will also start using it. The bad news is that the malware, being just another piece of source code, can be easily adapted to target any bank, not just those in Russia or Ukraine.
 14 DAY TRIAL //
14 DAY TRIAL //