A scan of the Alexa Top 10,000 sites by High-Tech Bridge Security revealed that despite the critical alert the OpenSSL project put out regarding this month's security update, many companies have still not patched their servers and remain vulnerable to dangerous HTTPS MitM (Man-in-the-Middle) attacks.
For the past year, the OpenSSL project has really stepped up its game in terms of security fixes, issuing new versions with hardened security on a monthly basis.
While most of the bugs are medium priority, once in a while, the project also puts out critical and high severity issues, which any system administrator should have the common sense to apply as soon as they're available for download.
Latest OpenSSL flaw allows HTTPS MitM attacks
The latest OpenSSL bug, CVE-2016-2107, patched at the start of the month of May 2016, is a Padding Oracle attack that affects only encrypted traffic that uses AES CBC ciphers, and when the server counterpart supports AES-NI (Advanced Encryption Standard New Instructions).
If these conditions are met, the attacker can launch a Web exploit and interpose himself between the server and the client, in a classic MitM attack that allows him to sniff HTTPS traffic and extract its content.
Because the AES-CBC cipher is considered the strongest cipher available for TLS 1.0, TLS 1.1, and also recommended by NIST guidelines and required by the TLS 1.2 RFC, the chances are that a huge chunk of HTTPS traffic is exposed to the CVE-2016-2108 vulnerability.
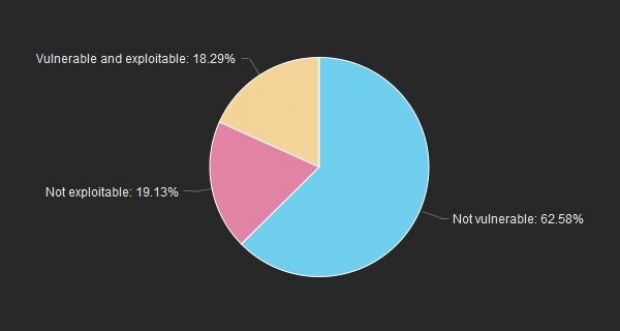
37.42% have not applied the latest OpenSSL patch
The quick scan High-Tech Bridge Security experts carried out revealed that 18.29 percent of all the scanned websites are vulnerable to the latest OpenSSL flaw, 19.13 percent are vulnerable - but other security measures prevent active exploitation - while 62.58 percent have done their due diligence and patched their infrastructure.
The automated scan looked at standard HTTPS ports (443), along with email-related ones such as 25, 110, 143, 465, 587, 993, 995.
Lack of time and update complexity leads to many servers remaining vulnerable
As for the reasons why these companies fail to patch these services, Ilia Kolochenko told Softpedia that "one of the main reasons is lack of time within the IT teams. Business introduces more and more requirements to stay competitive on a global level, implementing new systems and features every day, completely forgetting about security and risk management."
"Second reason is a relative complexity to patch. If you run a small server, updating OpenSSL shall not take longer than ten minutes, however if you have a cluster of several hundreds of servers serving millions of customers 24/7, even a simple patch may cause a downtime and other critical problems," Mr. Kolochenko told Softpedia. "This is why large companies are usually much slower to patch."
"Third reason may be related to this particular flaw: as it's not a critical RCE, sysadmins may put it into the very end of their To-Do, taking care of more critical issues."
If you'd like to test your server for the latest OpenSSL bug, the company also provides a free server testing service.

 14 DAY TRIAL //
14 DAY TRIAL //