Palo Alto Networks has revealed details about a malware distribution campaign taking place in Japan, where users are being targeted with malicious files spreading the Aveo trojan, a new malware variant recently discovered.
Based on the spam emails distributing this threat, and considering the usage of email lures and fake documents with Japanese text only, the crooks seem to be targeting Japanese users exclusively.
According to an analysis conducted by the security vendor, the Aveo trojan bears similarities to the FormerFirstRAT malware family, also known as DragonOK, which was detected in April 2015 was used in attacks against Japanese targets as well.
Aveo is a very simple threat, but dangerous nevertheless
Technically, the malware is very simplistic, according to malware analysts Josh Grunzweig and Robert Falcone. "Aveo is far from the most sophisticated malware family around," said the two.
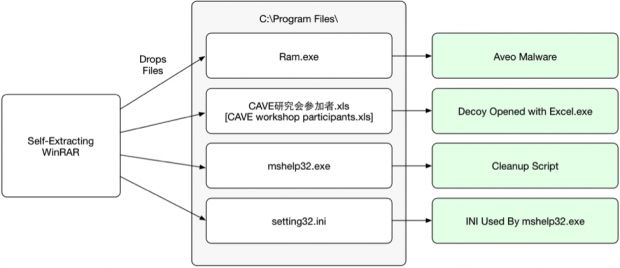
"Using a self-extracting WinRAR file, the malware drops a decoy document, a copy of the Aveo malware, and a cleanup script."
Crooks are spreading the Aveo malware using self-extracting binaries that use a Microsoft Office Excel icon. When users launch this file into execution, the Aveo malware installs on the PC but at the same time downloads an Excel file and shows it to the user to avoid raising any suspicions. As mentioned by the two analysts, a Batch script cleans up leftover files.
Basic backdoor features included
After this, Aveo works like a regular backdoor/RAT. It first registers with its C&C server, to which it communicates via an unencrypted HTTP channel.
From each infected computer, Aveo collects a unique victim hash, IP address, Microsoft Windows version, username, and ANSI code page identifier. This data is associated with each user and sent to the C&C server.
After this, the malware then waits for further commands. Palo Alto researchers found support for the following operations in Aveo's source code: execute command in interactive shell, get file attributes, write files, read files, list drives, and execute DIR command against path.
 14 DAY TRIAL //
14 DAY TRIAL //