With the help of security researcher Jack Whitton (fin1te), Microsoft has fixed a CSRF (cross-site request forgery) in its main authentication system used by services such as Azure, Outlook, and Office.
The flaw allowed an attacker to steal a victim's authentication token and then to use it to log into his accounts.
As the researcher describes the flaw's inner-workings on his blog, the issue was found in Microsoft's self-baked authentication system, which functions similarly to the OAuth protocol.
Attackers could have logged into Azure, Outlook, and Office accounts
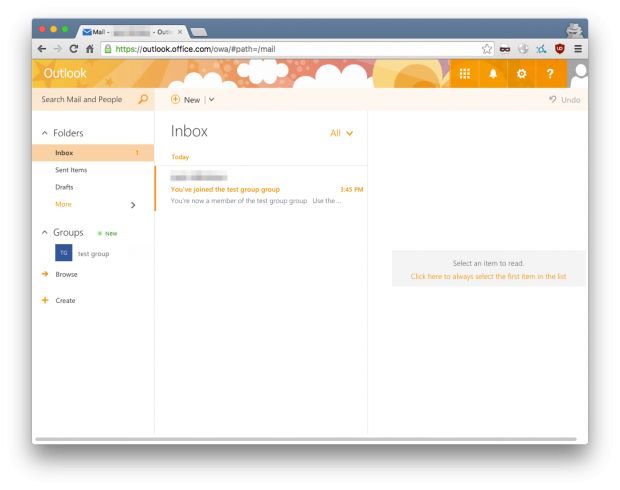
This system first intervenes when users are logging in via the classic login page on Azure, Outlook or Office. Users are redirected from this login page to Microsoft's centralized authentication system which can be one of the following URLs: login.live.com, login.microsoftonline.com and login.windows.net.
During this initial redirection, a parameter is added to the URL (wreply) which holds the user's origin login address, from where he's trying to authenticate.
Microsoft's login service verifies the user and then redirects him back to that URL, along with an authentication token which stands as a sign that the user has successfully proved his identity.
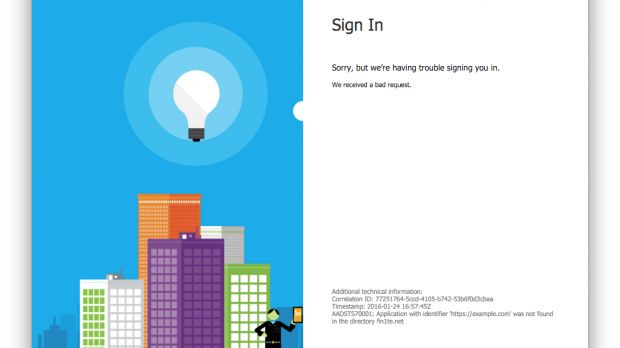
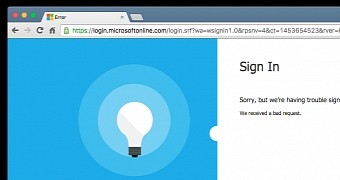
Whitton discovered that he could alter the "wreply" parameter in such a way to send the authentication tokens to a website under his control. This was possible due to improper input filtering on the wreply URL.
From there he could take the victims' tokens, craft a correct second-stage redirection back to the original login page, and access a victim's account without being detected.
Attack also relies on social engineering
For his attack to work, the user would have to click his maliciously-crafted (first redirection) link, and he should be already logged into one Microsoft account. Each token is valid for the service that issued it, but an attacker would gladly be happy with gaining access to one account at a time.
Whitton reported the issue to Microsoft at the end of January, who fixed it and awarded a $13,000 reward for his work. The company paid a similar reward to Wesley Wineberg last October, for a flaw in Microsoft's OAuth-based login system. Wineberg received $24,000 for his work in a period when Microsoft doubled bug payments for flaws in its authentication system.
Whitton is a well-known security researcher, being one of the top earners in Facebook bug bounty program.
@matttiko It wasn't in the double bounty promo like Wes's was unfortunately, but the payout was $13,000 so I can't complain! — Jack Whitton (@fin1te) April 3, 2016
 14 DAY TRIAL //
14 DAY TRIAL //