Localized fake payment form campaigns using injected scripts to target Magento-powered e-commerce websites from Italy and Bulgaria have been detected by the Sucuri website security service's research team.
Bad actors have continuously upgraded credit card stealing malware with new features and capabilities designed to hide in plain sight to take advantage of e-commerce customers' distraction.
"We’ve been regularly seeing injected scripts with URLs that either mimic or include a portion of the victim’s site domain," said the Sucuri research team. "Sometimes the injected code also references the victim’s site. Recently, we’ve come across another level of customization."
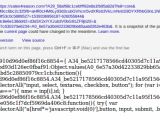
In a first instance, a Magento online shopping website was injected by bad actors with a script hosted at hxxps://elegrina[.]com/assets/.js and designed to replace the real payment form with a Bulgarian localized version, exfiltrating the stolen payment data to the elegrina[.]com domain.
The exfiltration domain was registered on November 18, and it used a hosting server from Russia to store the data stolen from infected online shops.
Localized payment form injecting scripts used to assail specific targets
Furthermore, Sucuri's researchers went on hunting for other websites infected by the same malware campaign but managed to find a single other instance, an Italian online retail site using a .com domain.
The Italian online shop used the same script that injected a localized payment form, this time using hardcoded Italian captions to allow potential Italian victims to navigate their way around the payment page easier.
According to the Sucuri researchers, "while localization of the malware adds additional complexity to the attack, it is definitely worth it from an attacker’s perspective."
Sucuri also found data stealer script injected within the Italian website which used POST Ajax requests to send payment details and site credentials stolen from online forms with the help of hijacked onclick handlers.
Even though the two different malicious campaigns did not show any evidence of being connected, they did prove the readiness of malware authors to put in the extra effort needed to customize their tools to attack specific targets while also being able to stay undetected throughout their mission.

 14 DAY TRIAL //
14 DAY TRIAL //