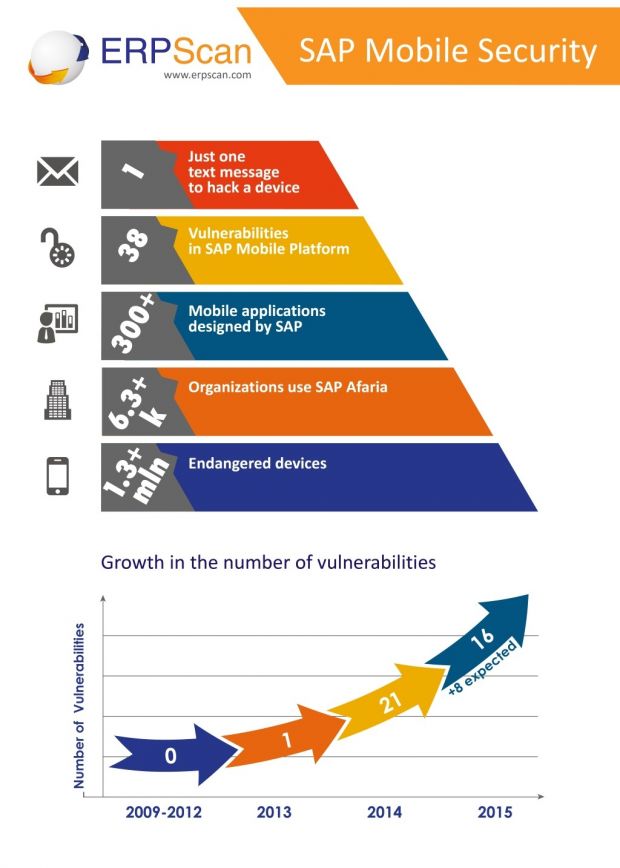
SAP's Afaria platform contained several security bugs which would have allowed attackers to take control of all mobile devices connected to it and even delete their data with one single maliciously crafted SMS message.
SAP is one of the world's leading enterprise software providers, known to a lesser degree to regular Internet users but very well-known to medium-to-large businesses.
One of the service's offerings is SAP Afaria, a software platform that facilitates BYOD (Bring Your Own Device) networks inside enterprises.
The platform works by providing client applications that are installed on employee phones, and a server component which the company's IT staff can operate to control who, when, and where can access company resources from their phone.
According to security researchers at ERPScan, the platform was plagued by numerous bugs, which the company has now fixed.
Attackers could have wiped phones with one SMS
One of the critical security vulnerabilities discovered allowed attackers to mimic one of the commands sent from the server component to the mobile client.
This command is usually sent in the form of an SMS message, signed by a SHA256 hash.
According to ERPScan researchers, attackers would have found it very easy to sign these message with their own hash, and then send their own commands to any mobile connected to the Afaria network.
The only things they would have needed were the phone's number and IMEI code, both of which can be acquired in multiple ways, as detailed by ERPScan's paper presented at the HackerHalted security conference in Atlanta, USA.
By spoofing these messages, attackers would have had complete control over the employees' phones, allowing them to lock them, disable WiFi functions, and even delete all the data on the devices.
Attackers could have taken control over the phones via the Internet
The second major vulnerability was a stored XSS in the Afaria administration console. Attackers would have been able to exploit this latter one by sending a maliciously crafted packet to a specific port, which would then be recorded and stored on the platform's admin section.
When an administrator would have logged in, that particular piece of JavaScript code would have been executed, indirectly giving the attacker access to the admin panel and all the connected devices.
Using this flaw in the SAP Afaria platform, attackers could have stolen information from affected devices or forced malware installations on all phones.
Three more bugs to round things out, all as severe as the first two
There were also three more security vulnerabilities discovered. The first was a buffer overflow which enabled the attacker to take complete control over the platform and even take it down completely.
The second was a missing authorization check which let attackers access the Afaria platform without any authorization procedures, indirectly giving them access to all of the network's data, while the third, another buffer overflow issue, caused DoS (Denial of Service) states that blocked access to the platform for all users.
As mentioned above, these vulnerabilities are now all fixed, even if it took SAP engineers longer than expected, this disclosure being planned for the Black Hat conference in Las Vegas that took place in mid-August.

 14 DAY TRIAL //
14 DAY TRIAL //