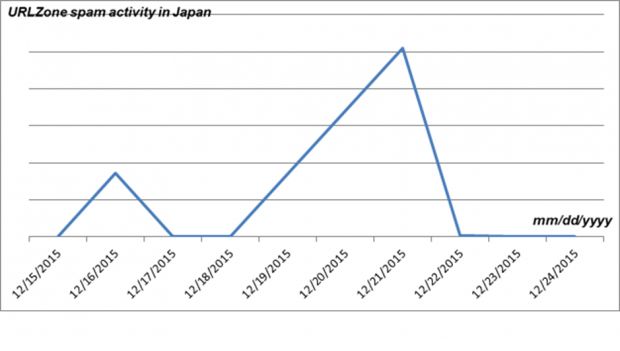
After the venerable Rovnix banking trojan was seen for the first time attacking Japanese banks during December 2015, it's now URLZone's turn to do the same thing and move its operations from Germany and Spain to the Land of the Rising Sun.
URLZone, first discovered in 2009, has only targeted European countries and has rarely moved out of its comfort zone, mainly because it was very good at its job, due to a huge arsenal of highly optimized spam campaigns, very efficient at delivering the malware's payload on their target's computer.
This changed after mid-December 2015, when FireEye's security team reported on the first instances of the URLZone trojan detected in Japan, about the same time IBM was also seeing the first Rovnix infections.
URLZone is delivered via spam messages (as always)
Just like Rovnix, URLZone relied on an intense spam campaign to spread to victims, and to fool users into executing the malicious payload, it often used two file extensions in the file's name so there would be a higher chance that an unsuspecting user would double-click the malware's executable.
As for the spam's source, most of it was sent via temporary email addresses registered just for this purpose on the site of Japan's biggest mobile carrier (Softbank) and Yahoo! Japan's email service.
For the infection per se, URLZone uses a nifty trick called "process hollowing," which suspends OS processes, empties their tasks, and fills the legitimate process with malicious actions.
URLZone steals your passwords and uploads them to a remote server
Once the trojan gets a foothold on the infected PC, the first thing it does is scan the system for various types of system details, which it collects and sends to a C&C server. Arbor Networks analyzed the C&C communications protocol in depth last August, and you can read a full technical write-up on their site.
After the trojan gets the go-ahead from the C&C server, URLZone will then, and only then, start collecting and exfiltrating various user details such as email addresses and passwords, the user's Windows address book, FTP credentials, and Web profiles and passwords. Most of this data is collected by hooking into legitimate applications such as FTP clients and Web browsers.
URLZone is also quite apt to get persistence on infected computers, being able to survive PC reboots, and it will also do its best to avoid executing when it detects that reverse engineering tools are also running on the PC.
"Although URLZone has been around for a while and primarily targets countries in Europe, we still see it active and now shifting to Japan," FireEye said in its URLZone advisory. "It is likely that URLZone will further expand its activity in Japan with improved localization and techniques."
FireEye is also reporting on another spam campaign that started on January 19, 2016, and advises Japanese users to be cautious when opening email attachments from unknown senders.

 14 DAY TRIAL //
14 DAY TRIAL //