A new twist in malware distribution was seen these past days by security researchers who observed an Android trojan that hides as a video player for pornographic movies and uses a multi-stage installation process to avoid antivirus detection.
The trojan, detected under different names by various antivirus makers, is distributed from rogue websites that advertise pornographic content.
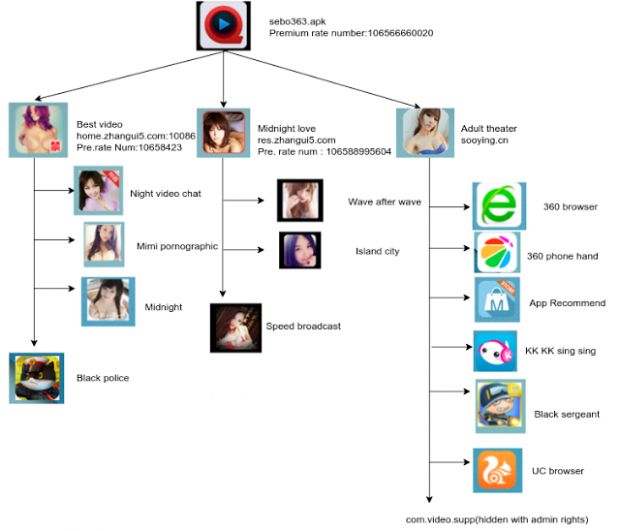
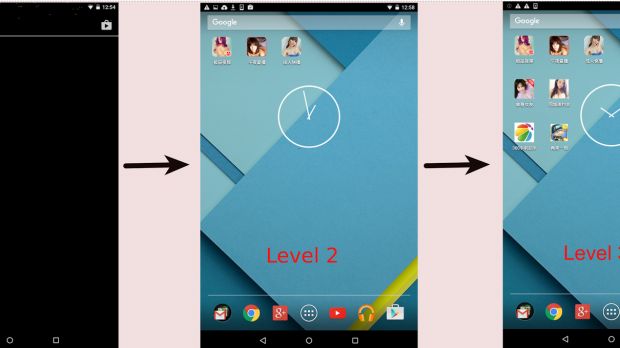
Users are told to download and install a special video player to view the adult movies, but when they execute the malicious Android package, the crooks install three other apps on the device.
Trojan uses three-stage installation process
This escalates even further, with the crooks forcibly installing a third wave of apps when the user clicks these three second-stage apps, which are also advertised as adult-themed applications.
The purpose behind this technique is to split malicious behavior between different applications, making it harder for security companies to detect and piece back their attack routine.
The trojan's main functions are for intercepting and sending SMS messages. The crooks use these apps to subscribe users to various types of premium services. When these premium services send an SMS verification code to each victim, the trojan intercepts it, and then sends the verification code back to the sender, as a sign of authenticity.
Trojan never gets root access, is easy to remove
Only the first app requires users to grant it permissions for sending SMS messages, which reduces the possibility of pornography-craving users of suspecting anything strange when installing the subsequent apps.
"The application uses the concept of pending intents, which allows another application to use your application's permissions to execute a predefined piece of code," Zscaler researchers explain the process which these different apps use to talk to each other, and coordinate their malicious behavior.
Researchers say that the trojan only targets a few SIM operators in China. Because the trojan does not include support for rooting the device, removing it is just like removing any other Android app.
 14 DAY TRIAL //
14 DAY TRIAL //