There's a way for attackers to unlock Android phones that have been protected using a password, as a security researcher who goes by the nickname of jgor has revealed.
The vulnerability (CVE-2015-3860) only affects recent Android devices, running OS version 5.0.0 to 5.1.0, and can be exploited by trying to authenticate on the lockscreen using a very long password string while the camera app is open.
The vulnerability only works when the lockscreen is protected with a password and it is not present on devices locked using PIN numbers or gesture patterns.
According to jgor's writeup, the attacker must have physical access to the phone for this flaw to be actively exploited.
The basic steps for carrying out such an attack
For starters, the attacker must first craft a long password string. According to jgor, this can be achieved by using the emergency calling window while the lockscreen is active.
Attackers can write text one character at a time, or they can copy and paste a small portion over and over again until the whole field is full.
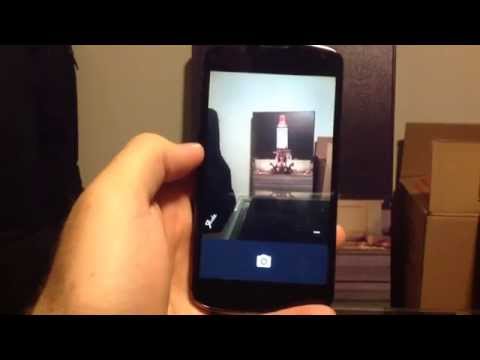
Once a long text has been copied to the phone's clipboard, the attacker can then open the camera app, which for Android 5.x can be done from the lockscreen by swiping up on the camera icon (which is always active).
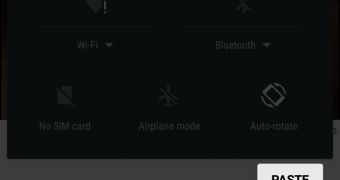
With the camera open, attackers can then pull the notifications panel down, and try to access the phone's settings section.
This automatically makes the phone ask the user for a password, and the attacker can then supply their long password string created before and stored in the phone's clipboard.
Crashing the camera app removes the lockscreen
Entering this text will destabilize the device, and eventually make the camera app crash. When this happens, the lockscreen is removed, and the attacker is redirected to the home screen from where they can extract the data they desire.
According to jgor, crashing the camera app varies in time, and sometimes might redirect attackers to an incompletely rendered home screen.
Google was informed of the vulnerability in late June, and it released Android 5.1.1 at the start of August to fix the issue. CVE-2015-3860 is also one of the security fixes included in Google's first ever batch of over-the-air security updates.
 14 DAY TRIAL //
14 DAY TRIAL //