According to data gathered by Sophos researcher Gabor Szappano, one exploit builder, an application for putting together booby-trapped Office files, is currently responsible for about half of all malicious Office files spread via email spam.
Szappano's exploit market estimation includes not only Office documents such as Word, Excel, and PowerPoint, but also PDF files, CHM help documents, and HTML pages (as HTA files).
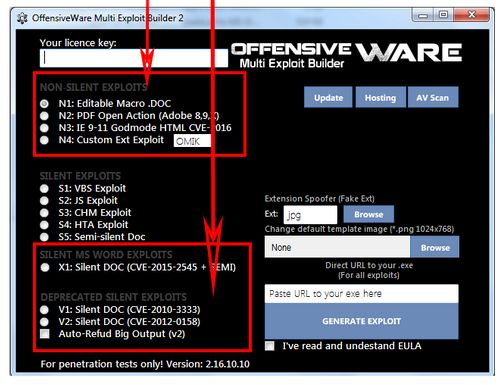
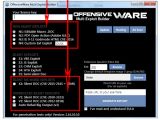
According to the researcher, a large amount of these types of malicious files are compiled using the Ancalog Multi Exploit Builder.
Polish developers behind Ancalog and OffensiveWare brands
In fact, Szappano reveals that the recently launched OffensiveWare Multi Exploit Builder is just a rebranded version of Ancalog, just like the OffensiveWare Remote Keylogger is a rebranded version of the Aaron Remote Installable Keylogger.
By pointing out source code similarities, source code comments, similar GUIs, and a similar mode of operation, Szappano connects all four applications, which he claims are most likely the work of a yet unidentified Polish developer.
What's for sure is that Ancalog (or OffensiveWare) is one of today's most popular exploit builders, despite not featuring support for the latest vulnerabilities.
Ancalog leverages old exploits
An analysis of the tool's capabilities reveals that Ancalog leverages ancient vulnerabilities such CVE-2010-3333 and CVE-2012-0158, for which vendors have issued patches for more than four years.
Support is also included for a newer vulnerability, CVE-2015-2545, but that exploit is very spread among all exploit builders thanks to publicly available proof-of-concept code.
Probably because of this, the infection success rate of Ancalog-created files is only a meager 1 percent, Szappano says, lower than the estimated 3.5 to 5 percent, the malware infection rate for all email-delivered malware.
"It sounds like a strange decision to use vulnerabilities that have been patched 6 and 4 years ago, especially as it’s unlikely that more than even 10% of users would be vulnerable to them," Szappano writes. "But the tool is frequently updated to bypass most security solutions. The criminals who use this tool must have chosen the ability to avoid AV detection over the ability to infect users."
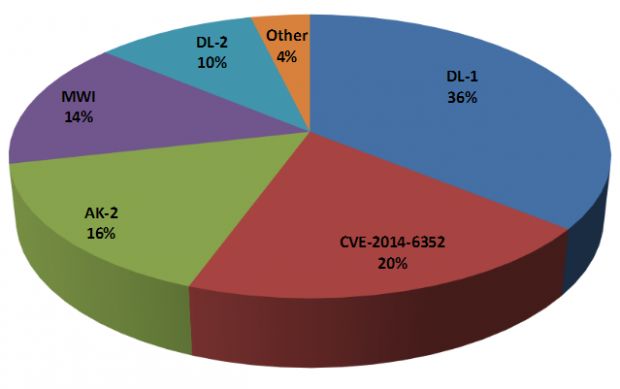
Ancalog has a market share of 46%
Ancalog's market share is around 46 percent, according to Szappano, who traced back the exploit builder's origins to February 2015, when the first version came out.
Initially, Ancalog was only a CLI tool written in Python, but as it became more popular, its coder added a GUI with the help of the Lazarus Free Pascal development environment. Currently, Ancalog, as OffensiveWare, goes for $290 for the full version, and $49 for the light package.
While the application's source code and license is peppered with mentions of "for educational purposes" and "for pentesting only," Ancalog's author is also very busy advertising his creation on underground hacking forums such as HackForum. As such, Ancalog's clientele is mainly made up of all sorts of criminal lowlifes.
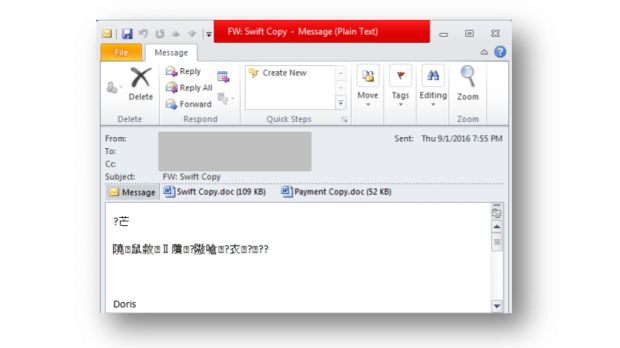
Szappano says he tracked much of Ancalog's usage to Russian and Nigerian BEC scammers, with one Nigerian group using a clever trick to increase their chances of success by distributing two Office documents, generating the two files via Ancalog with a different exploit in each file.
 14 DAY TRIAL //
14 DAY TRIAL //