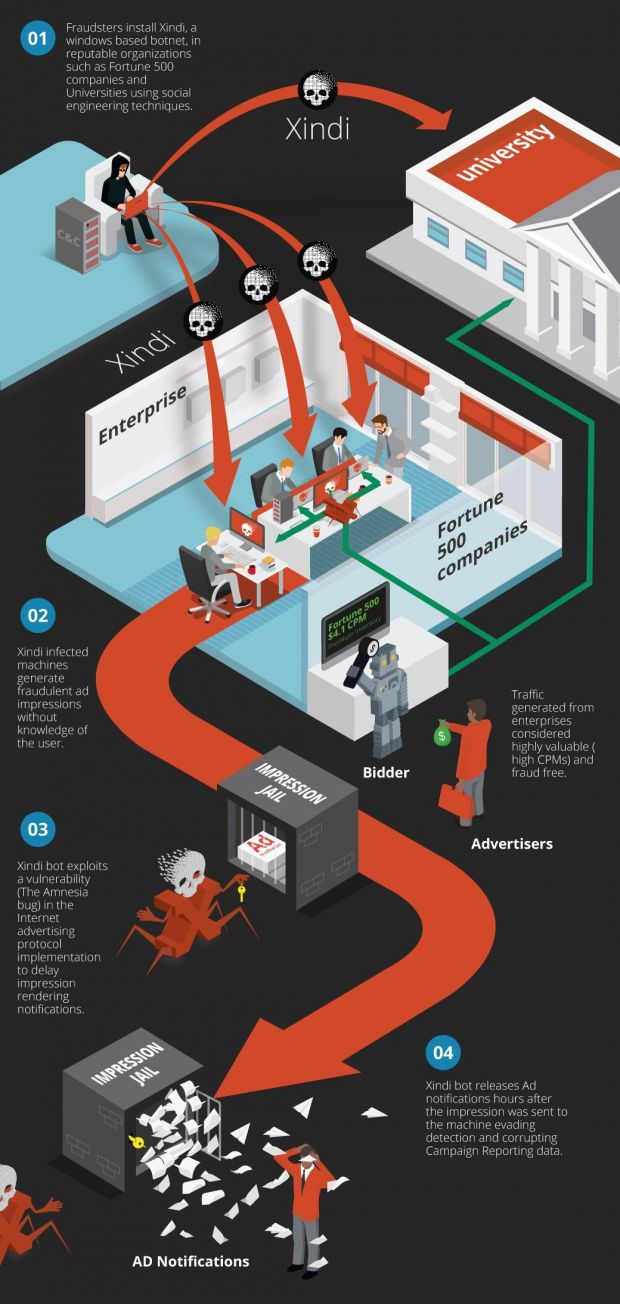
Online advertisers are at risk of losing billions by the end of 2016 if they don't find a way to stop the Xindi botnet from spreading, a botnet that leverages flaws in the OpenRTB advertising protocol to boost its owner's ad revenues.
OpenRTB is a protocol used for internal communications in online advertising. The protocol, in a simplified explanation, is used to interconnect advertisers, ad servers, and websites where ads need to be displayed.
The Amnesia bug, a flaw in the OpenRTB protocol
For the past year, a flaw in OpenRTB (CVE-2015-7266 - also known as the Amnesia bug) allowed (and still allows) an attacker to listen to OpenRTV ad messages but hold back receipt notifications for hours.
When weaponized inside malware, like the one used with the Xindi botnet, the Amnesia bug allows an infected machine to request numerous ads from the same advertiser and hold back notifications, making the ad network believe the ad failed and did not show. Later, when the notifications are released, the ad network is on the hook to pay all the impressions, even if not all ads were rendered inside a Web page.
Pixalate, an enterprise security and analytics platform, estimates that between 6 and 8 million computers have been infected with this malware, in more than 5,000 organizations.
Xindi botnet going after "reputable" targets
The Xindi botnet operators seem to be specifically targeting machines that are part of reputable Fortune 500 companies, universities or government agencies.
This is for two reasons. Advertising networks usually don't expect to see ad fraud from these targets and have fewer monitoring tools pointed at them, and all the aforementioned organizations have access to superior broadband connections when compared to home users.
Xindi botnet is active for more than a year
First signs of Xindi-powered attacks were recorded as early as October 29, 2014, and then again in quick bursts in following months like December 2014, March 2015, and August 2015.
Most infected targets are in the US and are usually running Windows 7 or Windows XP. The list of top affected advertisers includes big names like Uber, Home Depot, McDonald's, Honda, Pandora, Monster, Verizon, and Nissan.
Pixalate estimates that if ad networks don't fix the OpenRTB protocol flaw that permits this type of attack to be carried out, online advertisers could lose up to $3 billion / €2.8 from fake ad impressions by the end of 2016.

 14 DAY TRIAL //
14 DAY TRIAL //