Hundreds of thousands of people in China have been affected by a malware piece that is capable of remarkable feats, such as using Mac desktop computers to infect Apple mobile devices, regardless of whether they are jailbroken or not.
Dubbed WireLurker by researchers at Palo Alto Networks (PAN), the threat is distributed through 467 pieces of gaming software available in Maiyadi App Store, a third-party store for Mac apps in China that hosts premium pirated content.
The games would be repackaged with WireLurker and uploaded to the store. Researchers say that all malicious programs displayed a “Pirates of the Caribbean” wallpaper during the installation procedure.
Redundancy used to achieve persistency
In a report by Claud Xiao of PAN, it is stated that the compromising items have recorded more than 356,104 downloads in the past six months. Given the possibility to jump to any Apple mobile device connected to an infected Mac, WireLurker is likely to have impacted a number of users in the hundreds of thousands range.
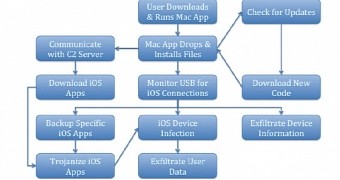
Once it reaches a computer system, the threat starts to communicate with the command and control (C&C) server, verifying for updates and downloading apps for Apple’s mobile devices, which are then trojanized.
Its process runs in the background at all times, monitoring the USB for iOS product connection, and upon detection, it sends the rogue apps through iTunes. Then, WireLurker proceeds to exfiltrate information relating to the device and the user.
Palo Alto Networks researchers have noticed that, in the latest version of the malware, the iOS apps are signed with enterprise certificates and communication to the C&C is encrypted.
Authors constantly improve the piece
Xiao notes that the server the malware contacts is set up at 124.248.245.78 (comeinbaby[.]com), where the malicious iOS apps are hosted and exfiltrated data (product serial and model numbers, phone number, Apple ID, Wi-Fi address, disk usage, and the unique device identifier – UDID) is stored.
Three different versions of the threat have been observed since April 30 through October 17, each of them gaining fresh functionality and code refinement.
At the beginning, it did not download and install iOS apps, but a subsequent release added this feature, which worked only on jailbroken devices. In the latest release, the authors included encrypted communication and the possibility to infect non-jailbroken products.
For compromising non-jailbroken devices, WireLurker signs the infected apps with enterprise certificates. In the case of jailbroken ones, it simply repackages software that has been backed up or downloaded to the device and then proceeds to installing or re-installing it.
According to the researchers, persistency is achieved through running more than one process on the affected computer because launching an infected application always loads malicious code in the background, ensuring contact with the command and control server and monitoring of the USB ports.
WireLurker is a significant threat for Apple consumers
“The ultimate goal of the WireLurker attacks is not completely clear. The functionality and infrastructure allows the attacker to collect significant amounts of information from a large number of Chinese iOS and Mac OS systems, but none of the information points to a specific motive,” writes Claud Xiao in the report.
One thing is certain though: the malware is under active development, meaning that it has not reached full maturity and new versions are very likely to emerge in the near future.
Researchers have already labeled it one of the biggest threats for iOS and OS X of all times, being the second piece that attacks Apple’s mobile platform through USB and the first one to automate repackaging of rogue apps; it is also the first in the wild sample that compromises a non-jailbroken device through enterprise provisioning.
Among the methods that can protect against it is the recommendation that generally goes for Android users: do not install apps from untrusted sources and limit access to content from properly curated locations, in this case Mac App Store.
In the case of jailbroken products, the advice is not to accept any unknown enterprise provisioning profiles. Maintaining everything updated and having an antivirus solution installed also helps.
 14 DAY TRIAL //
14 DAY TRIAL //