More than two years after the launch of Windows Store, Microsoft failed to curate the repository of apps claiming to be the official products of reputable developers, putting users at unnecessary risk.
In most of the cases, the fake apps do not have other purpose than to deceive users of the store into believing they’re the real deal, which is more often than not free of charge, and make them pay to download them.
What the victim gets in return of the money are most of the times instructions for downloading the legitimate app. In other words, users are scammed.
A quick look into the entries available in Windows Store revealed that Microsoft cares more about collecting hoards of apps than the quality of software offered to their users, thus sabotaging its own ecosystems.
A simple search earlier this week for popular products, showed multiple fake apps charging for something that could be obtained free of charge; and all of them were present on the first page of results.
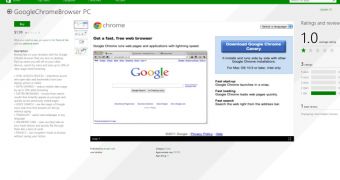
Some of the entries were obvious frauds, such as the one we found to be asking $4.99 / €3.76 for installing Google Chrome browser on the system. The name (InstallGoogleChrome) is enough of a hint to stay away from it.
However, this is a fortunate case, but with other products users may be easily fooled into shelling out the money. Numerous VLC clones were charging for what could otherwise be gotten for free.
Apple’s iTunes has not been spared, either, as crooks delivered a paid version ($8.99 / €6.77) that offers instructions on using and downloading the app from official locations. Firefox is shamelessly provided for a fee.
Apart from allowing scammers to make some money from less knowledgeable users, since Microsoft allows fraudulent content in Windows Store, the repository can also be used by cybercriminals to deliver malware on the entire Windows platform.
Third party Android market places are the number one factor for malware infections on Google’s mobile operating system; with Windows Store crooks have the advantage of hosting malicious apps in the official Microsoft repository.
At the moment, the amount of threats targeting the mobile Windows platform is quite low; this generally causes marketing departments (of any company) to tout their products as being among the most secure, in order to increase popularity.
As soon as popularity is increased, cybercriminals move their sight on them and the result is far from being a positive one for the customers.
“Whenever a big company creates an open platform for developers, it’s unfortunately always going to attract the wrong kind of attention. Scammers see these as a target and are increasingly abusing the trust that big brands have spent millions of dollars and years building,” said via email Jovi Umawing, malware intelligence analyst at Malwarebytes.
In the case of Windows Store, it seems that there are no other threats than the scammy apps, which can generally be avoided by paying a little attention (check the developer, description), even if Microsoft fails to curate the market place.
This week, Microsoft started to put some effort in cleaning Windows Store and the most obvious apps trying to deceive users into paying for free software. Scammy entries are still present but in a lesser amount.
Despite this sort of traps, Microsoft made sure that no malicious app is present in Windows Store. Malwarebytes did not see any apps laced with malware in the store and other antivirus vendors gave similar replies.
Jaromir Horejsi of Avast said in an email that their researchers could not find any threats in Windows Store, but told of an attack type that could be deployed on Windows Phone.
The risk scenario exposed has actually been observed to target Android phones, but the initial component could be executed on Windows Phones, too.
In the example provided, Horejsi says that attackers leverage in-app malicious advertisements, which redirect to a specific web page when accessed.
The landing page displays alerts about the mobile device being infected and offers to initiate a scan to identify the threats; a fake scanning process starts, at the end of which an app is offered for download.
The security researcher points out that this scenario was seen only on Android platform (via Tapsnake virus) and Avast did not offer any information about malware being present in Windows Store.
Microsoft already deployed the crackdown on scam software in its marketplace, and the most evident examples have disappeared. There are still entries to be removed in order to completely clean up the place, which are very likely to be eliminated in the near future.
A representative of the company told Slate that actions have been taken to improve the overall Store experience:
“We strive to make the Windows Store a high-quality experience for customers and also accessible to the broadest audience of developers. Based on customer and developer feedback, we recently took actions to help users discover the specific app titles they’re searching for and improve the overall Store experience.
“We recognize that there is more work to do and will continue to re-evaluate our policies to strike a balance between the opportunity for developers and the app quality that our customers expect,” they added.
[UPDATE, September 1]: Microsoft started to clean Windows Store of misleading apps. In an initial stage, the company deleted 1,500 entries and towards the end of August a few hundred more have been removed.
 14 DAY TRIAL //
14 DAY TRIAL //