Security researchers found a proof-of-concept (POC) vulnerability code that exploits the Remote Desktop Protocol issue patched up by Microsoft on March 13.
When the security update was made available, the Redmond company urged customers to apply the fix as soon as possible, especially since they were expecting that an exploit would be developed in the next 30 days.
It turns out that it took less than three days for someone to come up with a working POC.
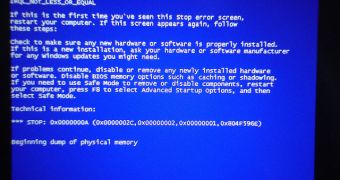
SophosLabs experts found one on a Chinese website that causes computers to crash. Unfortunately, there’s not a long way to go from this stage to the point where it can be turned into something far more serious.
“The code we've seen - in the form of Python scripts - attempts to exploit the MS12-020 RDP vulnerability and causes Windows computers to blue screen. It wouldn't be a surprise if whoever is writing this code to further develop the attacks to produce a fast-spreading internet worm,” Graham Cluley, senior technology consultant at Sophos, said.
There have also been reports of fake POCs, one of which developed by [email protected].
Microsoft fixes a lot of important and critical vulnerabilities each month, but once in a while we see one that can have devastating effects on the computers of users who fail to apply the appropriate patches.
Yesterday we’ve learned that someone already offered a bounty for anyone who could come up with a POC, so it shouldn’t surprise anyone that one (at least) is already made available.
Because who knows how things could be moving along in the underground market, it’s crucial that users understand that this is not something to joke about.
Those who for some reason can’t apply the updates are advised to enable Network Level Authentication which offers a certain degree of protection.
 14 DAY TRIAL //
14 DAY TRIAL //