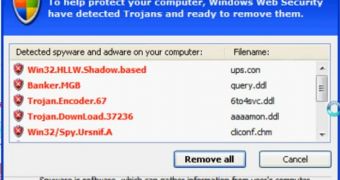
Fake antivirus programs that take over computing devices and hold them for ransom are not uncommon, researchers determining the many “purchase software” Google searches lead to such malicious elements.
Zscaler researchers found that many of these fake AVs are unchanged, being precisely the same as they were a few years ago, but since the task of promoting them and serving them to users is aided so much by search engines, there’s no need for the cybercriminals to change them too much.
It turns out that 95% of the search results for things like “purchase microsoft word” actually lead to hijacked websites that redirect the customer until eventually he/she is presented with a domain that serves a malicious antivirus.
Experts found that the domains that redirect users from hijacked sites to the fake AV pages are all hosted on Russian domains, their task being a simple one. All they do is tell apart real browsers from bots by utilizing a JavaScript to write a cookie and the read it.
If the cookie is retrieved, it means that a real internaut is visiting the hijacked site and a redirect to the fake AV page steps into play. If the cookie can’t be retrieved, the session is redirected to Bing or Google.
“Hopefully, one day Google will clean up the search results related to buying software as they did for the most popular searches. Until then, many users will end up on fake stores, fake AV pages or other malicious sites,” Zscaler’s Julien Sobrier writes.
In the meantime, until search engines clean up the search results, users are advised never to purchase software products from untrusted vendors. Also, an up-to-date antivirus program is always recommended as in most cases it can identify the malicious application’s real intentions.
 14 DAY TRIAL //
14 DAY TRIAL // 