Multiple vulnerabilities discovered in the website of a UK-based company called OnlineFX, which conducts foreign exchange services, can be exploited to extract highly sensitive data from the underlying database. Credit card details and customer information are possibly compromised.
According to its own website, OnlineFX is a financial company based in central London and offers foreign currency exchange at low rates, bank money transfers to over 70 countries, as well as IT, marketing and corporate services. The onlinefx.co.uk flaws were disclosed by Romanian grey hat hacker Unu, who specializes in finding SQL injection vulnerabilities in high-profile websites.
The hacker notes that a poorly secured parameter allows executing SQL queries in the database. However, because the database server is MSSQL, the results of the queries are not displayed in the browser window. This type of attack is known as a “blind SQL injection” and requires special tools to exploit.
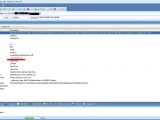
Unu used a specialized penetration testing application called Pangolin, developed by a Chinese security firm to see inside the database. According to the screenshots he published, the web server is running on Windows Server 2000 with a Microsoft SQL Server 2000 backend. Using the permissions obtained by exploitation of the flaw, Unu notes that he could have accessed anything on the entire computer.
The onlinefx1 database is of particular interest as it contains tables called Store_User_Info, Customer_Shipping_Info or Store_Order. Furthermore, the Store_Order table contains columns such as Card_No, Name_On_Card, Validation_Number and there are 77,726 records inside. Meanwhile, another table contains data such as customer login and password, first and last name, address, city, country, postal code phone or e-mail and the record count is 85,029.
Unu notes that he did not attempt to extract any information from the aforementioned columns as he is only interested in exposing vulnerabilities and not use them for malicious purposes. He also points out that the company did not reply to his attempts at contacting them.
Unu made his disclosure on Saturday and in an e-mail sent to us, he also revealed two other vulnerable parameters in the same website. Our messages sent yesterday morning to two different e-mail addresses belonging to the company also went unanswered.
Update: An OnlineFX spokeswoman has informed Softpedia over the phone that the vulnerabilities mentioned in this article have been addressed. She also noted that the company has thoroughly tested its website for similar flaws.

 14 DAY TRIAL //
14 DAY TRIAL //