Turkish cybercriminals are trying to distribute their malicious web browser extensions by uploading them to the official Google Chrome store.
Kaspersky experts say that hackers have turned to this technique after Google added some security mechanisms that prevent the silent installation of extensions.
In one scenario observed by Kaspersky, the attackers used Facebook to lure internauts to various websites hosted on .tk domains. These domains are set up to redirect visitors to a bogus Chrome update site.
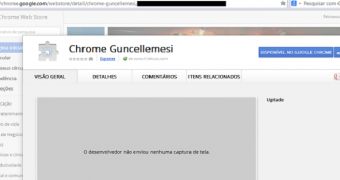
Those who choose to update are presented with instructions on how to do so and urged to download extensions called “Chrome Guncellemesi,” “Chrome Update” or “Flash Player 12.1” from the official Chrome Web Store.
Despite the fact that they’re hosted on a legitimate Google site, the extensions are malicious, since they ask the user for permission to access all the data on all the websites they visit.
Similar extensions have been found for Firefox as well.
Google has been notified and the company is struggling to keep the Web Store clean, but the cybercriminals keep uploading their creations.
 14 DAY TRIAL //
14 DAY TRIAL //