Security researchers from Vietnamese security vendor Bach Khoa Internetwork Security (BKIS) have identified a computer trojan, which copies itself over the update components of popular software. So far, Adobe Reader and Java Runtime have been targeted.
The malware, which Bkis has named the W32.Fakeupver.trojan, is written in Visual Basic and uses the technique to fool even experienced users. Malicious Trojans that employ file names similar or identical to known components in order to hide their process and startup routine are not new.
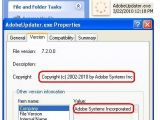
However, this trojan also imitates the icons and versions of the targeted programs. For example, checking the version information on the fake AdobeUpdater.exe file will show the developer as being Adobe Systems Incorporated and a "Copyright (c) 2002 – 2010 by Adobe Systems Inc" notice will also be displayed.
Furthermore, the researchers point out that the malicious executable is overwriting the original file, thus breaking legit functionality and making it harder to detect. "Ordinary users, sometimes even virus researchers themselves, are easily ‘fooled’ and skip such malware without raising an eyebrow," said Nguyen Minh Duc, senior security researcher and security director at BKIS.
The trojan creates a registry entry called Adobe Update Manager under HKLM\Software\Microsoft\Windows\CurrentVersion\Run pointing to where the legit AdobeUpdater.exe should normally reside. Otherwise, a file named AdobeUpdater.exe appearing in a process or startup listings with a different path would look very suspicious.
After infecting a computer, the trojan starts several services if they are not already running, including DHCP client, DNS client and network share. It also opens a special port in order to listen for commands from the hackers.
Adobe is not the only company whose products are targeted by this threat. The update component from Oracle's newly acquired Java Runtime Environment is also masqueraded and deleted. BKIS has seen a variant of this trojan using the "C:\Program Files\Java\jre6\bin\jucheck.exe" path and file name.

 14 DAY TRIAL //
14 DAY TRIAL //