Trojan.Peacomm is a Trojan horse designed to build peer-to-peer botnets out of compromised machines. Security company Symantec has tracked the evolution of the Trojan and concluded that the initial outbreak of the Trojan.Peacomm detected in January 2007 and labeled as the storm-worm war was only the seed of what is still to come. The fact of the matter is that Trojan.Peacomm has continually evolved since January and Symantec concluded that the initial attacks were simply a way of test driving the Trojan and determining its capabilities to build peer-to-peer (P2P) bot networks.
"There were many elements that led us to believe that the initial Trojan was rushed. For example, the internal timestamp of many of the Trojan's files shows that they were compiled only a few hours before being spammed, which indicates that the authors were making last-minute changes. Additionally, the rootkit code was quite buggy and included a mistake that allowed users to remove its hooks by simply running a "net stop" command," revealed Elia Florio, Symantec Security Response Engineer.
Florio opined that the authors of the Trojan.Peacomm choose a simple solution, that of transforming the malware into a Trojan downloaded instead of adding functionality. Still, that was back in January. In mid April 2007, the Cupertino-based company detected yet another consistent spam run of Trojan.Peacomm, but this time the Trojan came in more sophisticated variants.
Trojan.Peacomm.B is the latest example of Trojan.Peacomm identified by Symantec. The security company informed that this variant can now detect virtual environments such as VMWare and VirtualPC.
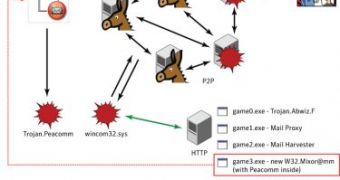
"The bad news about Trojan.Peacomm.B is the new rootkit driver, which now uses a randomly generated name ("windev-[rand]-[rand].sys"). This hidden module, which is injected into the SERVICES.EXE process, is XOR-encrypted. Additionally, this module is almost 90 kb bigger than its previous version. The reason for the extra size is that code from the downloaded Trojans is now inserted directly into the Peacomm.B module. This is shown figure 2 (below), which is a comparison of some strings of Peacomm.B and the old mail-harvesting component," Florio added.
One crucial observation that Symantec has made is the fact that the machines that are infected with previous and more primitive versions of Peacomm are updating themselves with the evolved and more sophisticated variants of the Trojan.
"On the P2P botnet, we have seen several metadata packets containing the encrypted URLs of the updated variant to download. Once decrypted, the filenames are usually "3ti.exe," "cent.exe," and "inst.exe," and are downloaded from a number of locations," Florio concluded.
 14 DAY TRIAL //
14 DAY TRIAL //