Researchers from Budapest-based security firm CrySyS Lab have investigated a cyber-espionage campaign, dubbed “TeamSpy,” that’s been targeting information from high-profile organizations, including government ones, from Hungary, Russia, the Middle East, France and Belgium.
The company began investigating the cyberattacks after being notified by the Hungarian National Security Authority, which detected targeted attacks against the country’s systems.
While some of the victims of this campaign appear to be regular users, diplomatic, research and industrial targets have also been identified.
For instance, a government organization from Hungary, an electronics company with government ties from the Middle East, an industrial manufacturer from Russia, a NATO/EU embassy in Russia, and research and educational organizations from Belgium and France.
Part of the toolkit used in the attacks appears to have been utilized since 2010. However, the most interesting part about this campaign is that it relies on the popular remote access tool TeamViewer to observe victims, steal files from them and perform other malicious tasks.
The cybercriminals install a legitimate version of TeamViewer on their victims’ devices, but they alter its behavior with DLL hijacking to ensure that it stays hidden.
“In addition to the TeamViewer based campaigns, we also saw signs indicating a number of older attacks based on proprietary malware with C&C server based control. We estimate the number of distinct campaigns to be in the order of tens,” CrySyS experts noted.
It appears that the attackers are mainly after private crypto keys, passwords, iOS device history from iTunes, OS and BIOS data, and other information they can obtain via screen captures and keylogging.
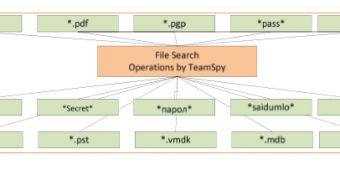
The files they look for are office and PDF documents, and anything else that contains strings such as “pass,” “secret” and variations of these words in Georgian and Russian.
The detailed technical report on TeamSpy is available here.
 14 DAY TRIAL //
14 DAY TRIAL //