An experiment aiming to discover what happens with the data that ends up in the hands of cybercriminals after a breach or a cyber-attack revealed that a stolen cache traveled across five countries and three continents in the first few days.
The project was set up by security vendor Bitglass, provider of data tracking and watermarking technology, which created a fake database containing sensitive information that would be appealing to the cybercriminals.
Database was all honey for crooks
Once the bogus cache was complete, the researchers released it on the Dark Web, the part of the Internet where search engines and the regular Joe do not usually venture. The websites on this part of the online world, which is also the home of TOR anonymity network, are accessed via special tools, such as the Tor browser.
Bitglass relied on a custom tool to make up, among others, names, social security numbers, payment card information, addresses and phone numbers. The total amounted to several thousand and all was saved in an Excel spreadsheet and released on the Dark Web.
The technology developed by the company applies a unique fingerprint to the files, which can later track how many times the document was accessed and the geo-location the action occurred in.
Cybercrime hotspots record most activity
“The speed at which the bait was taken was staggering. In the first few days, the data had reached over 5 countries, 3 continents and was viewed over 200 times,” the report informs.
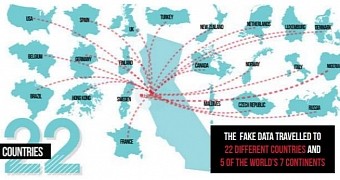
After 12 days, the file had received more than 1,081 clicks and had circulated through 22 countries, on five continents.
The list of countries it reached includes the US, Belgium, Brazil, Nigeria, Hong Kong, Russia, Spain, Germany, UK, France, Finland, Sweden, Norway, Denmark, Italy, Turkey, and Canada.
Obviously, most of the clicks were tracked to countries associated with increased cybercrime, such as Russia, China and Brazil.
The researchers say that based on analysis of time, location and IP addresses, a high rate of activity from two groups was recorded, one operating from Nigeria and the other from Russia.
According to Bitglass, most of the data loss is the result of malware and hacks, which account for 53% of all breaches. Furthermore, an incident of this type takes 205 days to be completely mitigated.
 14 DAY TRIAL //
14 DAY TRIAL //