In a world where companies fight a permanent battle to keep their infrastructures safe against cyberattacks, enterprise security and cloud-based systems take the main stage.
After yesterday we’ve heard from a real black hat hacker what needs to be done to properly protect a website, now we’ll learn the opinion of an expert on the matter of securing an enterprise network.
Carl Herberger, VP of Security Solutions at one of the leaders of the industry, Radware, was kind enough to answer some questions on how large businesses are handling the migration to the cloud and why state organizations in most cases fail to protect their infrastructures.
Softpedia: Before we start, please tell our readers a bit about yourself and your position at Radware.
Carl Herberger: As Vice President of Security Solutions at Radware, I am responsible for developing, managing, and increasing the company’s security practice in the Americas. Before joining Radware, I served as V.P., Security & Compliance, a major East Coast Cloud Security provider based in Philadelphia. I’ve also ran Information Security for Campbell Soup and Barclaycard US and from 2002 to 2006, I was the senior executive in charge of the SunGard Professional Services IT Security Practice which was recognized as one of the top-five IT security consulting organizations in the U.S. in 2005.
Lastly, and perhaps most notably, I also served as a U.S. Air Force officer as an Electronic Warfare Officer (EWO) on B-52H aircraft, with my last duty serving the Pentagon. While at the Pentagon, I evaluated computer security events affecting daily Air Force operations. Softpedia: One of your company’s specialties is to make sure enterprises who rely on cloud-based technologies know how to properly secure their infrastructure. From what you’ve seen so far, how are businesses handling the migration to the cloud, are they up to the challenge? Carl Herberger: Cloud has been a challenge for nearly all companies who need to migrate and thus far the success record has been spotty at best. From our perspective there are unique threats to cloud operations in which most enterprise companies have either never faced or the threat was so remote that it fell into the 90/10 rule of not worthy of addressing through operational controls. These are as follows:
1. APIs. APIs are HEAVILY used in cloud operations and often define the ‘secret sauce’ within a cloud company’s reporting and customer service management. However APIs secretly have a very dark side as the security and availability of general cloud services is now almost totally dependent upon the security of these basic APIs.
From authentication and access control to encryption and activity monitoring, these interfaces must be designed to protect against both accidental and malicious attempts to circumvent policy. Today the Cloud Security Alliance calls APIs the #2 threat to cloud operations and it is our feeling that these little tools will rise to represent the single biggest problem in cloud operations going forward.
Furthermore, organizations and third parties often build upon these interfaces to offer value-added services to their customers. This introduces the complexity of the new layered API; it also increases risk, as organizations may be required to relinquish their credentials to third parties in order to enable their agency. API are at once a powerful business tool and a very much overlooked vulnerability.
The vulnerability exists for two reasons: - Lack of widely distributed enumeration tools - Lack of education on mostly a network-oriented security team - Most APIs which are leveraged are for seemingly innocuous devices – such as load balancers, customer-service applications, network device reporting, etc.
Bottomline: Care needs to be exercised when using APIs.
2. Managing Availability. Yes, most companies indeed outsource to cloud providers for INCREASED availability, however there is one thing to have a contractual statement to an SLA and actually achieving these results in today’s threat (e.g. DDoS) environment. If availability is that valuable to you, you should consider the following buying guidelines before migrating to the cloud
2012 Considerations before Buying an Attack Mitigation System
Managing the security of critical information has proven a challenge for businesses and organizations of all sizes. Even companies that invest in the latest security infrastructure and tools soon discover that these technology-based “solutions” are short-lived.
From antivirus software to firewalls and intrusion detection and prevention systems, these solutions are, in fact, merely the most effective strategies at the time of implementation. In other words, as soon as businesses build or strengthen a protective barrier, the “bad guys” find another way to get in.
Attackers are constantly changing their tactics and strategies to make their attacks and scams as damaging as possible. The good news is that it appears that attacks and subsequent defenses are breaking down in categories which can be measured systematically.
The following areas are of a particular concern as we look towards 2012 planning for attacks:
1. Real-Time Protection against Volumetric Attacks: According to Wikipedia, volumetric attacks are defined as the following, “attack involves saturating the target machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable.
Such attacks usually lead to a server overload. In general consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.”
2011 has seen a dramatic rise in the growth of these attack types and even more ominous is the procurement of more capable ‘weapon systems’ or new application-based tools from which attacks can be launched. The following is a list to consider when making certain you are covering your basis in this category:
a. TCP SYN floods b. TCP SYN+ACK floods c. TCP FIN floods d. TCP RESET floods e. TCP Fragment floods f. UDP floods g. ICMP floods h. IGMP floods i. Packet Anomalies j. Known DoS tools
2. Application Layer (L7) Availability Protections: Malware is morphing in scale, scope and delivery payloads. It has managed to renew itself as a top concern related to protecting your organization in 2012 and has emerged as an imminent threat to Organizational Availability.
In fact, attackers have shifted away from mass distribution of a small number of threats to micro distribution of large families of threats. These new strains of malware consist of millions of distinct threats that mutate as they spread rapidly.
In this category, the following is a list of attacks worthy of considering when choosing protection mechanisms for your enterprise:
Real-time protection against: a. Bot-originated and direct application attacks b. HTTP GET page floods c. HTTP POST floods d. Customized / Additional HTTP Method attacks e. HTTP uplink bandwidth consumption attacks f. DNS query floods (A, MX, PTR,…) g. Brute Force Attacks (HTTP, Telnet, POP3, IMAP, etc.,) Advanced behavioral application monitoring: h. HTTP servers real time statistics and baselines i. DNS server real time statistics and baseline
3. Service Cracking Behavioral Protections: Trusted Web sites are the focus of a large portion of malicious activity. As more and more users go online to take advantage of Web 2.0 applications — like social-networking sites, blogs, and wikis — authors of ‘hacking and cracking’ software are right behind them, opening up yet another front in the constant cat-and-mouse game between security defenses and hackers.
These threats will become increasingly important with younger workforces who are proficient with these tools. To thwart these attack types consider very strong protections against these categories of attacks or threats:
a. HTTP servers b. Web vulnerability scans c. Bruteforce d. SIP servers (TCP & UDP) e. SIP spoofed floods f. Pre-SPIT activities g. SIP scanning h. SMTP/IMAP/POP3,FTP,etc i. Application Bruteforce j. Application scans
4. IPS & Reputation Services: The continued high volume of Hacktivist attacks underscored the importance of various signature prevention technologies to prevent proper exploitation of an evolving tool landscape.
In fact, the heavy reliance on tools as part of Hacktivist attacks have ironically exposed the over-reliance on the perimeter model of deployed security devices without IPS technologies on the VERY edge.
Most DDoS Providers do not rely on signatures and frequently fail to uncover newly developed attack tools, and most IPS providers suggest deployments of their tools to deep in the infrastructure for them to be meaningful to stop attacks at the perimeter.
The following is a shopping list of things to consideration when procuring IPS & Reputational Management solutions to prevent perimeter attacks:
Signatures Protection against: a. Application Vulnerabilities and exploits b. Web, Mail, DNS, databases, VoIP c. OS Vulnerabilities and exploits d. Microsoft, Apple, Unix based e. Network Infrastructure Vulnerabilities f. Switches, routers and other network elements vulnerabilities g. Malware h. Worms, Bots, Trojans and Drop-points, Spyware i. Anonymizers j. IPv6 attacks k. Protocol Anomalies
Security Operation Center l. Leading vulnerability security research team m. Weekly and emergency signature updates
5. Network scanning and malware propagation Protections: As mentioned above in the Application-focused problem of bots and malware, the very same categorical problem exists at the network layer, however this time it is as equally as important to protect the internal environment as well as the external in real time. The following is a list of network protection considerations:
a. Behavioral Real-time protection against Zero-Minute Malware Propagation and network scans: b. UDP spreading worms detection c. TCP spreading worms detection d. High and low rate network scans e. Scanning/spreading pattern identification f. Infected source identification Softpedia: Some decided to take an incremental approach when it comes to implementing cloud systems. Is this the best way to go, or should companies replace their old systems all at once?
Carl Herberger: Migration to the cloud is so varied from infrastructure, to voice, to data, to application, that a wholesale assessment with a blanket statement would be premature. I think the situation is dependent, and that any use case can be successful supported.
Softpedia: Security is a major issue when it comes to cloud based systems, especially since a lot of sensitive and corporate information is at stake. What is the best way to handle cloud security without interfering with the business workflow?
Carl Herberger: At the moment, I am an advocate of only private cloud operations should there been any security concerns what-so-ever. In addition, I believe this private-cloud requirement should be followed up with full shrouding (e.g. VPN, IPSEC, etc) communication between the two entities and a committed hard operational ‘carve out’ of systems within the cloud operator who can commit to true multi-tenanted operations.
Softpedia: I know that you occupied a position at the Pentagon. Judging by the fact that you’ve been on both sides, is a state organization better capable of handling security than private enterprises?
Carl Herberger: I truly feel like governments (at all levels) have massive inherent problems which make them incredibly less secure and less capable of stopping attacks.
Some of these reasons are as follows: - No one person is responsible, thus makes no one responsible - Architecture is a mesh which no one really understands and this mesh is linked together like a chain-linked-fence……so the overall security is dependent on the security of the weakest link. - Inability to respond quickly. The bureaucratic system is such that decisions are made by committee and take time. - Tools are inadequate - - dependent on an archaic procurement system which rewards price and not key features or quality - On a one-to-one basis, the employees securing our government are not as talented as the ones dedicated to some of our most esteemed private institutions - Secrecy. The government uses an old-fashion system of data privacy which actually prevents security personnel from conducting full and thorough audits and securing infrastructures from end-to-end.
So, there are, of course, some nice reasons why government is supremely situated to conduct security better than private enterprises and these are as follows:
- Generally when a government realizes they were breached the can be no end to the amount of resourced they can deploy including money, people, political pressure and the long arm of the law. - Government is uniquely situated to be able to counter international based threats and subpoena private entities for valuable information which is generally unavailable to private security personnel. Softpedia: What is your prediction related to cloud security? Will things get better for companies or will cybercriminals remain in the lead in this never-ending battle?
Carl Herberger: Security is like a chess match whereby there is a constant ebb-and-flow between the recognition of new vulnerabilities and new risks and the deployment of new controls.
Given this, there are no doubts that the cloud service model will go through a phase whereby nearly all will question the security models as the perpetrators will have found a huge exposure. I truly see an event which will have us question the integrity of our data and use of cloud services.
Moreover, corporate and external auditors are falling behind in their procedures and technical ability to audit this space. Once this ‘honeymoon’ phase is passed through, only then will we have a better handle of how secure the cloud, the talent and tools needed to do so and the true risks associated with cloud operations.
Honestly, from where I sit, one day companies who chose a very conservative internal business operational model will be rewarded for people who are looking for ‘clean’ data - - that is data which is trustworthy and hasn’t been tainted by a cloud operation. Softpedia: How exactly can Radware help organizations protect their virtual assets?
Carl Herberger: For the last year network security professionals around the globe have watched as a group of cyber hacktivists dismantled the web defenses of some of the most respected financial and ecommerce sites and “walked right in to” their secure data bases and holdings to make a statement.
These attacks were not the work of the numerous and very prolific organized crime syndicates whose botnets are constantly prowling and seeking network vulnerabilities to exploit for criminal financial gain, but stem from a group of hacktivists who happened to disagree with these particular companies adherence to a governmental request.
Like some amorphous story-book villain lurking in the shadows, this group known as Anonymous, took a vote among its secret “star chamber” of members and decided to punish these large credit card and financial organizations for following simple law enforcement to not process payments for a group known as WikiLeaks.
In early March of this year, Anonymous set their sights squarely on the finance industry with their A99 – Operation Empire State Rebellion.
Their Manifesto includes statements such as: • Above all, we aim to break up the global banking cartel centered at the Federal Reserve, International Monetary Fund, Bank of International Settlement and World Bank. • We demand that the primary dealers within the Federal Reserve banking system be broken up and held accountable for rigging markets and destroying the global economy, effective immediately.
Clearly the requirements of the A99 movement are questionable, but the ability of this organization to make good on their threats of engaging ‘in a relentless campaign of non-violent, peaceful, civil disobedience’ have been proven effective.
This is the threat landscape all network service providers face today, not just on a day-to-day basis but every minute-by minute. Many forms of attacks on your network are known and more easily defeated but the most daunting attacks are those whose form is not known, not yet seen or perhaps not yet recognized.
There are also the attacks that are known, but the modes in which the attacks are leveraged are not known. That is why perimeters are successfully being compromised. In the case of most of the recent attacks, the customary way of deploying security technology is not able to defend against these new attackers.
To be effective, a defense system must first be able to identify the attack as it is forming or in process of attacking the network. Second, it must determine which incoming traffic has a malicious intent and which is traffic is legitimate.
The legitimate traffic must be allowed to pass so that commerce can still be conducted and the illegitimate traffic must be quarantined from the rest of the network and dispensed. In addition, a network defense system must cope with various and multiple attacks in real time.
Standard network-security solutions depend on static signature protection against known application-vulnerability exploits and rate-based protection against high-volume attacks and unknown attacks.
Static signature-protection technology, deployed by Network-IPS, firewalls, and anti-viruses, can only identify predefined attacks. This type of traditional perimeter security relies on periodic signature updates, leaving the business vulnerable to zero-minute attacks, and offers no solution against non-vulnerability–based attacks.
Rate-based technology is designed to suppress abnormal traffic patterns. This technology is deployed as means of mitigating high-volume attacks or zero-minute attacks. However, a rate-based solution does not differentiate between attack traffic and legitimate traffic. Packets and sessions, good and bad, above predefined thresholds are dropped.
Rate-based technology offers no protection against lower-rate attacks (for example, brute-force attacks, low rate malware propagation, slow network and application probes). Furthermore, rate-based technology cannot prevent improper-use scenarios where attack traffic such as an HTTP page flood appears identical to legitimate application requests as in a flash crowd.
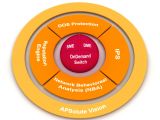
Radware’s DefensePro Attack Mitigation Solution
Radware’s award winning DefensePro is a real-time network attack prevention device that protects your application infrastructure against network & application downtime, Application vulnerability exploitation, Malware spread, Information theft and other emerging network attacks. DefensePro includes a set of security modules - DoS Protection, NBA, IPS and reputation engine - to fully protect networks against known and emerging network security threats.
Intrusion Prevention System
The Intrusion Prevention System (IPS) module is based on stateful static signature detection technology with periodic signature updates and emergency updates in case of a newly discovered high risk attacks.
Network Behavioral Analysis
The Network Behavioral Analysis (NBA) module employs patented behavioral-based real-time signature technology. It creates baselines of normal network, application and user behavior. When an anomalous behavior is detected as an attack the NBA module creates a real-time signature on- the-fly that uses the attack characteristics and start blocking the attack immediately. In case of DDoS attacks it injects the real-time signature into the DME hardware offloading the main CPUs from the excessive unwanted traffic.
Denial-of Service Protection
The Denial-of Service (DoS) Protection module is based on several technologies: signature detection, behavioral based real-time signatures and SYN cookies mechanism that challenge new connections prior to establishing a new session with the servers.
Reputation Services Engine
The reputation engine offers real-time Anti-Trojan and Anti-Phishing service, targeted to fight against financial fraud, information theft and malware spread.
These are the guiding elements of Radware’s Attack Mitigation System. We are unique in our approach and successful in practice, as proven by our ability to repel and withstand even Operation Payback’s attacks.

 14 DAY TRIAL //
14 DAY TRIAL //