Social engineering is the top malware propagation tactic, according to the Microsoft Security Intelligence Report Volume 11 Report(SIRv11), which includes data harvested in the first half of 2011.
The report reveals that social engineering is used more than any other techniques to spread malicious code, and that more traditional methods, such as exploiting vulnerabilities, simply pale in comparison.
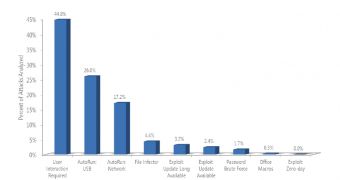
In SIRv11, the software giant notes that no less than 44.8% of threat propagation tactics require user interaction. Such threats include socially engineered malware, designed to trick victims into compromising their own machines.
“User Interaction Required - When a user has to perform an action for the computer to be compromised. In this usage, “action” means an intentional action that is in some way distinguished from typical use of the computer,” the Redmond company explains.
By comparison, malware which abuses the AutoRun feature in Windows accounts for 43.2% of malware threat propagation methods, even two the percentage is the sum of two different tactics, one involving USB storage while the other relying on network volumes mapped to drive letters.
“More than a third of malware detections that were analyzed were attributed to malicious software that misused the AutoRun feature in Windows,” the company states.
“To combat these threats, Microsoft took several steps to help protect customers, including releasing an automatic update for the Windows XP and Windows Vista platforms in February 2011 to make the Autorun feature more secure, as it is by default in Windows 7.”
Only approximately 6% of malicious code is designed to exploit vulnerabilities in software in order to infect computers, over seven times less than malware using social engineering to spread.
“None of the top families in the MSRT (Malicious Software Removal Tool) were documented as using zero-day exploits in 1H11,” Microsoft added. “Out of all the vulnerability exploitation detected by the MMPC (Microsoft Malware Protection Center), less than one percent was zero-day exploit activity.”
 14 DAY TRIAL //
14 DAY TRIAL //