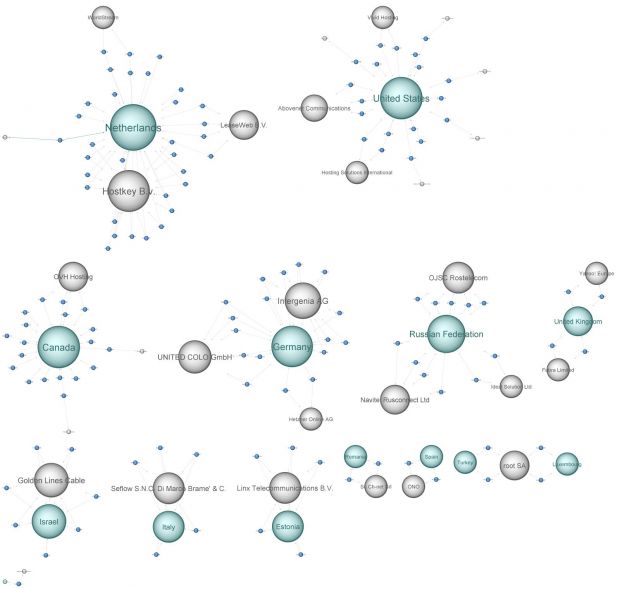
An operation carried out by law enforcement in cooperation with private security companies took down the Simda botnet, a network that included over 770,000 infected computers in 190 countries, regulated from 14 command and control (C&C) servers.
Ten of the control machines were located in Netherlands, while the rest were found in the United States, Luxembourg, Poland, and Russia.
Simda integrates detection evasion tactics
The takedown operation was led by the Interpol and engaged the efforts of Microsoft’s Digital Crimes Unit, as well as security firms Trend Micro, Kaspersky, and Japan’s Cyber Defense Institute.
Simda malware has been making victims since 2009, and apart from distributing other threats, it can also pilfer passwords and banking information from the compromised system.
Analysis from security researchers reveals that Simda relied on certain tactics to avoid being caught by antivirus products, such as detection of virtual environments and emulation tools, which are specific to malware analysis.
Vitaly Kamluk from Kaspersky says that server-side polymorphism and a short lifespan of the bots are other reasons that enabled it to escape detection.
One of the features observed by the researchers is Simda’s ability to modify a compromised system’s HOSTS files. Trend Micro says that this led the user to malicious websites whenever they tried to access legitimate ones.
“Our research shows that the malware targeted popular sites including Facebook, Bing, Yahoo, and Google Analytics, as well as their regional counterparts: e.g., Yahoo Singapore, Bing Germany, etc.,” Trend Micro researchers say.
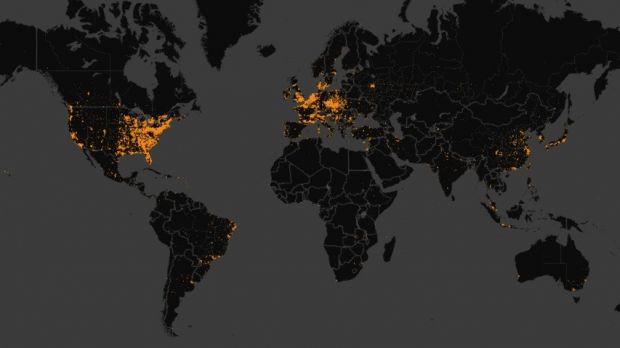
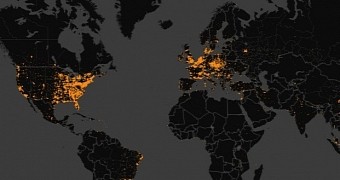
Most infections detected in the US
As far as infections are concerned, in a period of six months, Microsoft recorded about 128,000 new compromises each month, all made by a single Simda variant. Telemetry data from the company showed that the top ten most affected countries accounted for 54% of the infections.
The US was most impacted, 22% of the detections being detected in this country, as per data from Microsoft. Following at a large distance are UK (5%), Turkey (5%), Canada (4%), and Russia (4%).
Interpol confirmed on Monday that most of the infections were in the US, informing that about 90,000 computers had been compromised in this country in January and February 2015 alone.
Although the malware can no longer communicate with its operators, it should be removed from the system. Free scan tools have been developed and published by antivirus vendors. Microsoft offers Safety Scanner (Security Essentials is also fit for the job), Trend Micro included the routines in HouseCall, Kaspersky makes available Security Scanner, and Cyber Defense Institute created a tool for both beginners and more experienced users.
 14 DAY TRIAL //
14 DAY TRIAL //