A new report released by the US Government Accountability Office reveals that in the past 5 years the number of security breaches in federal networks have increased constantly, regardless of the measures implemented by the authorities.
The analysis is based on reports coming from 24 major national agencies collected between September 2010 and October 2011.
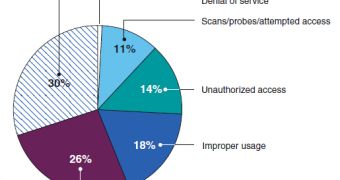
The figures show that in 2006 there were just over 5,000 incidents reported, while in 2010 the number skyrocketed to 41,000. 30% of the incidents from last year were attacks in which malicious code was injected into the networks of federal organizations.
Denial of service attacks represent only 1% of the whole number, but on the downside, 26% of the issues are still under investigation.
In the fiscal year 2010, 11 major organizations reported significant deficiencies in the security system that safeguards their information.
To show the efforts made by the big players in order to mitigate the impact of cyberattacks, the 24 agencies reported that 92% of the users with log-in privileges have been trained each year to raise the awareness on social engineering tricks, while 88% of the employees with significant responsibilities had received a more specialized schooling.
According to NextGov, the computers that form the national networks are vulnerable because proper protection policies have not been put in place.
Gregory C. Wilshusen, GAO director for information security issues, believes "These shortcomings leave federal agencies vulnerable to external as well as internal threats."
"As long as agencies have not fully and effectively implemented their information security programs, including addressing the hundreds of recommendations that we and inspectors general have made, federal systems will remain at increased risk of attack or compromise."
The paper concludes “Inadequacies exist in access controls, which include identification and authentication, authorization, cryptography, audit and monitoring, boundary protection, and physical security,” and as long as the companies don't properly implement the security programs “federal systems will remain at increased risk of attack or compromise. “
 14 DAY TRIAL //
14 DAY TRIAL //