Samsung Smart TVs equipped with Voice Recognition feature send information to a third-party speech-to-text service, but they are also making the delivery via an unencrypted channel, a researcher discovered.
Samsung’s Voice Recognition capability allows a user to issue voice commands to the TV, which are interpreted as commands for the device to carry out.
Samsung changes Privacy Policy
Last week, news broke about the feature recording more environmental sound than it should and sending it to the third-party service (Nuance Communications) for conversion into instructions for the TV.
The company has adjusted its Global Privacy Policy, which previously stated that “if your spoken words include personal or other sensitive information, that information will be among the data captured and transmitted to a third party through your use of Voice Recognition.”
Now it says that voice commands are collected only when the TV’s microphone is activated by saying a phrase like “Hi TV” and that only associated text is captured, for the purpose of improving the Voice Recognition feature.
However, another concern was the way the data was delivered, which should be done via a secure channel (HTTPS).
HTTPS port is used, but no encryption present
David Lodge from Pen Test Partners carried out an experiment to see if the traffic between the client and the Nuance Communications server was encrypted and whether eavesdropping was possible.
It turns out that Samsung uses only the standard port for HTTPS (443/TCP) and does not scramble the information to make it unreadable, should someone intercept the communication.
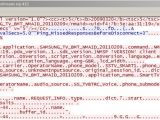
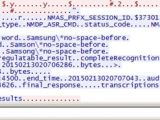
The researcher collected the data using Wireshark, which showed everything in the clear. He noticed that the network inspection utility presented a mix of XML and a custom binary data packet instead of encrypted information.
The choice for the HTTPS port is logical because firewalls with standard configuration allow traffic out of the network through port 443, but he could not understand why it was not protected.
From the traffic capture, Lodge was able to see the details about the device (MAC address, operating system version), as well as the voice commands he issued and what the TV understood of them. Additionally, a binary that most likely contained the audio recording has also been caught.
Surprisingly, Lodge found that an IP address that was not assigned to the TV he used for the test was also present in the traffic details.
“Based on the limited information leaked above in plaintext, there’s plenty to suggest that interesting data is making its way on to the interwebs from your TV. Come on Samsung, how about at least protecting it with SSL?” concludes the researcher.

 14 DAY TRIAL //
14 DAY TRIAL //